What Is Penetration Testing?
In today’s world, security is more important than ever. As organizations increasingly rely on technology to drive business, digital threats are becoming more sophisticated, varied, and difficult to defend against. One of the most effective ways to safeguard an organization’s digital assets is through penetration testing (or just “pen testing” for short). In this blog, we will explore what penetration testing is, why it’s vital for modern businesses, and how it fits into an organization’s overall security strategy.

What is Penetration Testing?
Penetration testing is a method used to evaluate security by simulating an attack from malicious outsiders (who do not have authorized access) or insiders (who have some level of authorized access). The goal is to identify vulnerabilities, weaknesses, or misconfigurations that could be exploited by attackers.
It should be noted that penetration tests are not necessarily always focused on technology. These tests can encompass other vectors, such as physical penetration testing and social engineering tests.
Penetration testing should be about more than just running automated scans—penetration testing involves the manual exploitation of systems by pen testers to assess how far they can breach a network, application, or system. Pen testers seek to mimic real-world attack techniques to uncover gaps in security that could otherwise go unnoticed.
Types of Penetration Testing
Penetration testing can be applied to a wide variety of environments, each with its own methodologies and tools. Some of the most common types include:
- Network (External, Internal, and Assumed Compromise) Penetration Testing:
Focuses on discovering vulnerabilities in internal and external network infrastructures, firewalls, and other network-based services. During this test, testers will perform activities such as port scans, mapping the network’s attack surface, and then performing attacks ranging from launching exploits against unpatched software services to relaying internal network traffic. - Web Application Penetration Testing:
Examines the security of websites and web applications. Common vulnerabilities tested include SQL injection, cross-site scripting (XSS), and authentication flaws. - Mobile Application Penetration Testing:
Involves the testing of mobile applications against a variety of attacks. This can include authentication flaws, script-based attacks, and injections.
- Social Engineering Penetration Testing:
Involves manipulating or deceiving employees into divulging sensitive information or performing actions that compromise the security of the organization, such as phishing attacks. - Wireless Penetration Testing:
Tests the security of an organization’s Wi-Fi networks and connected devices. Popular attacks performed during this test include MAC address spoofing and deauthentication attacks. - Physical Penetration Testing:
Evaluates the physical security controls of an organization by attempting to gain unauthorized access to buildings, servers, or other critical assets. During this test, you can expect a tester to try picking locks, social engineering employees, or cloning badges. - Red Team Assessment:
An assessment where the tester assumes the role of an advanced threat. Red teaming exercises can involve any of the above techniques as a means of attempting to gain entry.

Why is Penetration Testing Important?
Penetration testing serves as an essential component of a robust cybersecurity strategy for several reasons:
- Identify Vulnerabilities Before Attackers Do:
Regular penetration testing helps identify security gaps before real attackers can exploit them. This proactive approach allows organizations to strengthen their defenses by applying patches or mitigating security risks. - Simulate Real-World Attacks:
A penetration test goes beyond automated vulnerability scans by employing the same techniques that would be used by malicious hackers, giving companies a real-world picture of their security posture. This allows for the test to happen in a controlled setting instead of at the hands of a cyber criminal. - Meet Compliance Requirements:
Many industries are subject to regulatory standards such as PCI-DSS and HIPAA, which mandate regular security assessments, including penetration tests, to ensure compliance. - Evaluate Security Controls:
It’s not enough to simply have security controls in place. A penetration test assesses whether these controls are functioning as intended and whether they are robust enough to fend off attackers. - Enhance Incident Response Capabilities:
Pen tests help organizations prepare for potential attacks by identifying weaknesses in their incident response procedures. A good test can uncover deficiencies in how well an organization detects, responds to, and recovers from an attack.
The Penetration Testing Process
A typical penetration test generally follows these key phases:
- Pre-Engagement: Scope Definition and Rules of Engagement:
Before testing can even begin, the penetration tester and the client need to meet and share in an important discussion – scoping and expectations. This conversation usually takes place over a “rules of engagement call” (RoE call). The RoE call serves to establish scope, expectations, and considerations for both the tester and client and to ensure that both parties are on the same page. Timelines are discussed, as are deliverables, communication expectations, and any exceptions that may need to be excluded for testing – be they certain types of attacks or target hosts. This ensures that the penetration test is not only productive but is also performed in a safe way that minimizes the chance of complications arising as a result.
- Planning & Reconnaissance:
Before the test begins, the penetration tester gathers information about the target through both active and passive means, identifying the systems, applications, and infrastructure that are in scope.

For social engineering and physical penetration tests, it is not uncommon to rely on gathering information from the internet or passive resources and avoid interacting with the target. For example, a tester may case the internet to see if they can locate images of an employee’s badge. This image can then be used by a tester to assist in creating a fake badge for an on-site visit.
- Scanning:
During the scanning phase, testers use a variety of tools to map the network and detect potential vulnerabilities.
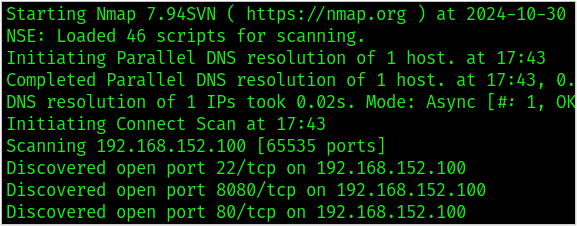
For physical tests and social engineering engagements, this phase can take the form of performing more active forms of reconnaissance, such as gathering seemingly innocent information over phone calls or casing the exterior of a building to identify camera locations and types of badge readers.
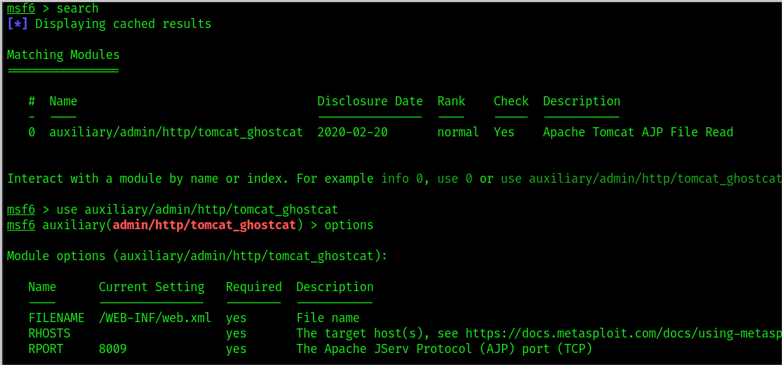
- Exploitation:
Here’s where the real testing begins. The ethical hacker attempts to exploit the vulnerabilities found during the scanning phase, using techniques like privilege escalation, SQL injection, or remote code execution to gain deeper access to the system.
For social engineering, a tester may make calls to employees and present them with ruses in an effort to harvest sensitive information.
- Post-Exploitation:
After gaining access, the tester will assess how much damage they could inflict, such as stealing sensitive data or escalating their privileges to an administrative level.
For social engineering engagements, this step of the process may involve looking to see what sensitive parts of the building can be accessed after security has been bypassed. Likewise, a social engineer may begin using compromised accounts to see what services inside of the network can be accessed.
- Reporting:
Finally, the results are compiled into a comprehensive report detailing the vulnerabilities found, their risk levels, and recommendations for remediation.

A strong report will also contain a detailed methodology that describes how the attacks took place and the results of each step. These steps can include helpful information, such as screenshots and commands used during testing, to better illustrate the exact process of the test.
Some Concluding Words
Penetration testing provides organizations with a clear understanding of their security weaknesses, allowing them to address vulnerabilities before they are exploited by malicious actors. As cyberattacks continue to rise in complexity, businesses that invest in regular penetration testing will be better equipped to defend against attacks.
Read more in our “Infosec for Beginners” blog series:
- How to Get a Job in Cybersecurity
- John Strand’s 5 Phase Plan For Starting in Computer Security
- From High School to Cyber Ninja—For Free (Almost)!
- Blue Team, Red Team, and Purple Team: An Overview
- Pentesting, Threat Hunting, and SOC: An Overview
- What Is Penetration Testing?
- How to Perform and Combat Social Engineering
- The Human Element in Cybersecurity: Understanding Trust and Social Engineering
- Build a Home Lab: Equipment, Tools, and Tips
- Questions From a Beginner Threat Hunter
- Shenetworks Recommends: 9 Must Watch BHIS YouTube Videos
- Mental Health – An Infosec Challenge

