The Top Ten List of Why You Got Hacked This Year (2023/2024)
by Jordan Drysdale and Kent Ickler

tl;dr: BHIS does a lot of penetration testing in both traditional and continuous penetration testing (CPT) formats. This top ten style list was derived from an analysis of our findings across our penetration testing services.
Anywho… This list is based on the last couple years of analyzing our report findings, mostly the findings that lead to compromise. We threw out stuff related to SSL and TLS, SSH ciphers, and yeah, we biased our study results a bit doing so. However, little has changed in the last few years. We still use the same and similar techniques as the previous ten years to gain initial access, move laterally, execute code, escalate privileges, access database content, and generally make a mess.
Number 10: Firewalls
This finding should read more like “Lack of Firewall-Based Restrictions.” Your organization should really enable East-West firewalls on workstations and servers where appropriate. Allowing everyone unfettered access to their workstation network is a serious risk. If you actively disable workstation and server firewalls with group policies, we advise you to begin unravelling the cultural history of this configuration, because it is not a great strategy for security. Actually, it’s a terrible strategy. We also consider a lack of network segmentation and generalized any:any rulesets across your VLANs and routable networks to be a concern.
In our opinion, the most dangerous port you have exposed is SMB TCP port 445. Close it– and don’t let it egress your network.
Remote procedure calls allow for everything from configuration changes to security memory access. It is time to start reducing this exposure.

Number 9: Message Integrity
Don’t know what this means? That’s normal and okay.
Message integrity checks (MICs) provide the foundation for validating who sent or started a conversation.

Additionally, this may mean proving oneself to a remote file share via a quick message digest exchange validated by a client and a server. Simpler yet? A service checks to make sure you are who you say you are.
Why? Message integrity checks reduce and mostly eliminate the effectiveness of credential relay attacks. The two primary relay attacks we use as attackers are SMB relay and LDAP relay. Both of these protocols support message signing.
SMB Signing: https://learn.microsoft.com/en-us/troubleshoot/windows-server/networking/overview-server-message-block-signing
LDAP Signing: https://learn.microsoft.com/en-us/troubleshoot/windows-server/active-directory/enable-ldap-signing-in-windows-server
Number 8: Defaults

Default configuration settings include things like:
- Default machine account quota
- Lack of SMB and LDAP signing
- High fidelity endpoint logging
- Really bad password policies
- NTLM authentication
- unProtected Users
- Enrollee Supplies Subject (ADCS ESC1)
- LLMNR, mDNS, and NBNS
- LAPS passwords in clear
- SCCM and MECM credentials
- Panther unattend.xml
- Browser WPAD
- Attack technique blindness
There are a lot of ways to take advantage of these weak default settings. As testers, we use some combination of the previous list to establish a foothold, escalate permissions, and move around networks.
Number 7: Patching
The next screenshot was taken from CISA’s equivalent, albeit different, interpretation of the why you got hacked in 2023 list: https://www.cisa.gov/news-events/cybersecurity-advisories/aa24-317a.
These findings hurt not only because of the ever-increasing speed of exploit weaponization, but because of the common discoveries that indicate even the last few years of vulnerabilities with patches haven’t been addressed.
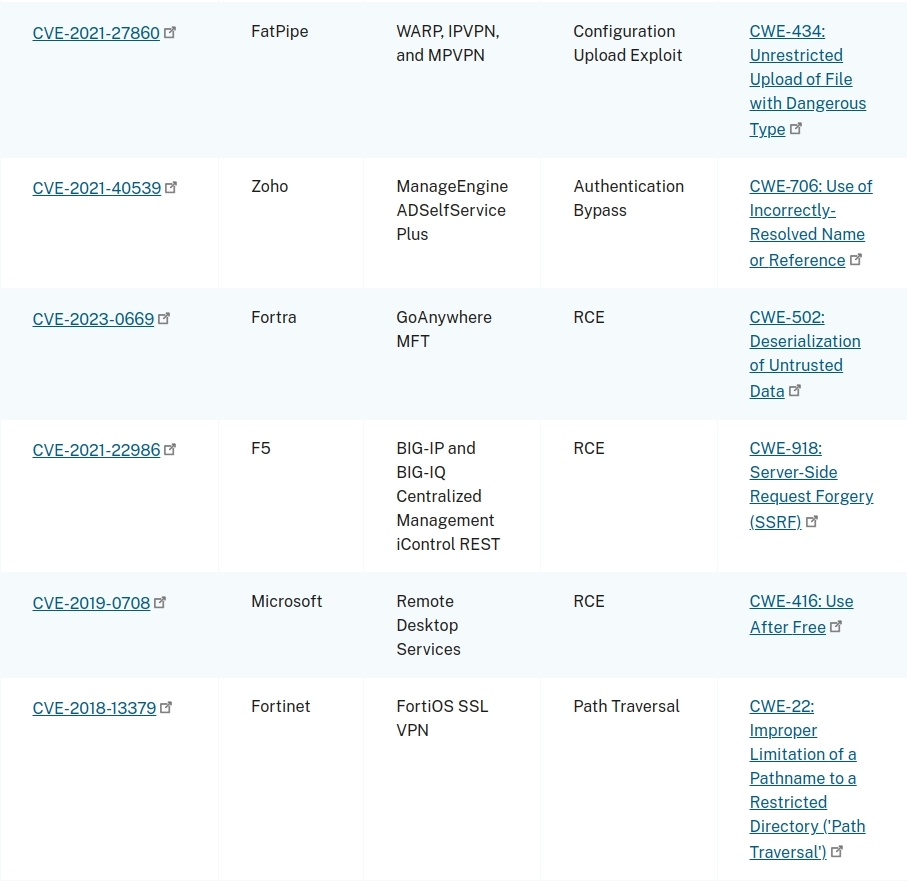
What did you notice here? Some routine, patchable vulnerabilities are still accessible to our adversaries. Apparently, per CISA, in sufficient numbers to warrant being reported.
From the perspective of someone who spends a lot of time assessing the security of internal networks, I can attest that patching is difficult. Maintaining support contracts is hard. Keeping appliances, software packages, and network gear updated is a very heavy lift. Inventory controls are also difficult to maintain.
Number 6: Weak Protocol Abuse
Is LLMNR still hanging around? Are browsers still requesting WPAD configuration? Is mDNS still lurking?

Yeah, and all these protocols still result in compromise.
Number 5: Web Apps
What could be more worrisome than exposing something to the internet? How about exposing an application with multiple outdated and vulnerable framework components? Add in an authentication component and address tracking and purchase history. Let’s not forget that somewhere the application is likely to store email addresses, usernames, and passwords too.
A basic e-commerce site all of a sudden sounds like carrying the weight of the digital world. By all appearances, the simple fact that applications are exposed to adversary networks 24/7, means that the constancy of vulnerability discovery is reality. A lot of these vulnerabilities go unreported until firms figure out there’s an active campaign targeting a specific set of services.
Regardless of all that, we report a lot of vulnerabilities associated with web applications, their framework components, underlying coding libraries, code logic, validation and input related issues, and session management tidiness.
Number 4: Employees
A story was shared recently via a cameo at Wild West Hackin’ Fest. Our continuous penetration testing (CPT) team’s number one initial entry technique up through October 2024 was help desk calls, social engineering, and password resets.

Number 3: Optics
Threat optics as a class of detective capability is improving. That said, compromise is still taking a long time to get detected. Per IBM, who like Verizon, does an annual and ongoing macro-breach assessment and statistical analysis, some things are improving:

This article contains another heavy hitting quote: “Businesses are caught in a continuous cycle of breaches, containment, and fallout.”
Number 2: ADCS
Please investigate your certificate environment. The consistency of domain compromise via weak enrollment templates and web enrollment services may be waning, but… The ADCS attack chain is a five-minutes-to-complete compromise scenario.

Do not get this wrong. Audit your templates. Enable auditing on your certification authorities.
https://github.com/ly4k/Certipy
https://github.com/GhostPack/Certify
Number 1: Credentials
Weak password policies result in users with weak passwords. The 90-day rotation cycle has resulted in the SeasonYear password disorder… As organization leadership, we can strive for better — passphrases!?
File shares, scripts, source code, and description attributes are still providing the means to escape limited privilege.
Browser data leakage and infostealers have produced a trove of emails, usernames, and passwords. Because of password reuse, there’s a new serious problem – your employees’ passwords have likely been used to create accounts outside of your enterprise. Once breached, the cycle of breaches, containment, and fallout continues.
Monitor for data breaches. Know your exposure.

So, that’s the list in its basic form. If we get some traction or interest in additional breakdowns in what we see on our engagements, maybe we can do some follow up blogs in a series.
Cheers as always and thanks for reading!
-jd / ki
Want to learn more mad skills from the folks who wrote this blog?
Check out these classes from Kent and Jordan:

