Introduction to Zeek Log Analysis
In this video, Troy Wojewoda discusses the intricacies of Zeek log analysis, focusing on how this network security monitoring system can be used to understand traffic and analyze logs effectively.

In this video, Troy Wojewoda discusses the intricacies of Zeek log analysis, focusing on how this network security monitoring system can be used to understand traffic and analyze logs effectively.
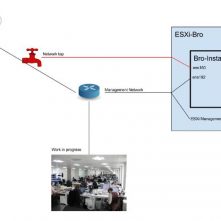
Kent Ickler // You’ve heard us before talk about Bro, an IDS for network monitoring and analysis. We’ve had several installs of Bro over time here at BHIS. It’s about […]

David Fletcher // Whenever I have the opportunity, I like to perform packet collection on a test for about five minutes so I can analyze the results and look […]

A Guest blog by Matthew Pawelski // A C2, or command-and-control, is used by attackers to control compromised systems. Most of these C2s are in control of large botnets, yet […]