Dynamic Device Code Phishing
rvrsh3ll // Introduction This blog post is intended to give a light overview of device codes, access tokens, and refresh tokens. Here, I focus on the technical how-to for standing […]

rvrsh3ll // Introduction This blog post is intended to give a light overview of device codes, access tokens, and refresh tokens. Here, I focus on the technical how-to for standing […]

Sally Vandeven // We have all heard people talk about how much cooler Linux is than Windows, so much easier to use, etc. Well, they are not necessarily wrong… but we […]

Sally Vandeven & David Fletcher // This is the podcast version of Sally & David’s webcast. For the whole webcast see our webcast post. Links that are mentioned in this […]
Podcast: Play in new window | Download
Subscribe: Apple Podcasts | Spotify | Amazon Music | RSS

David Fletcher & Sally Vandeven// Join David “Fletch” and Sally as they explore the cornucopia of wonderful, free tools in the SysInternals Suite that conveniently are signed by Microsoft and […]

Jordan Drysdale & Kent Ickler // In this webcast, we demonstrate some standard methodologies utilized during an internal network review. We also discuss various tools used to test network defenses […]

Beau Bullock // Overview Microsoft Exchange users have the power to grant other users various levels of access to their mailbox folders. For example, a user can grant other users […]
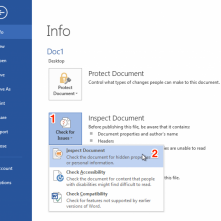
Ethan Robish // In my last two posts I showed how to insert tracking bugs in both .docx (Part 1) and .xlsx files (Part 2). But don’t let all that effort go […]

Ethan Robish // If you’re familiar with ADHD and Web Word Bugs, you likely already know the method to create web tracking software using .html files renamed as .doc files. […]