Rotating Your Passwords After a Password Manager Breach
| Ethan Robish It’s been nearly a year since Lastpass was breached and users’ encrypted vaults were stolen. I had already migrated to a different password manager for all my […]

| Ethan Robish It’s been nearly a year since Lastpass was breached and users’ encrypted vaults were stolen. I had already migrated to a different password manager for all my […]

Kent Ickler // Because, you know—that should be a thing. TL;DR: Don’t run the Unifi Controller on a laptop in the closet. BACKGROUND Ubiquiti’s Unifi controller is a network device, or software […]
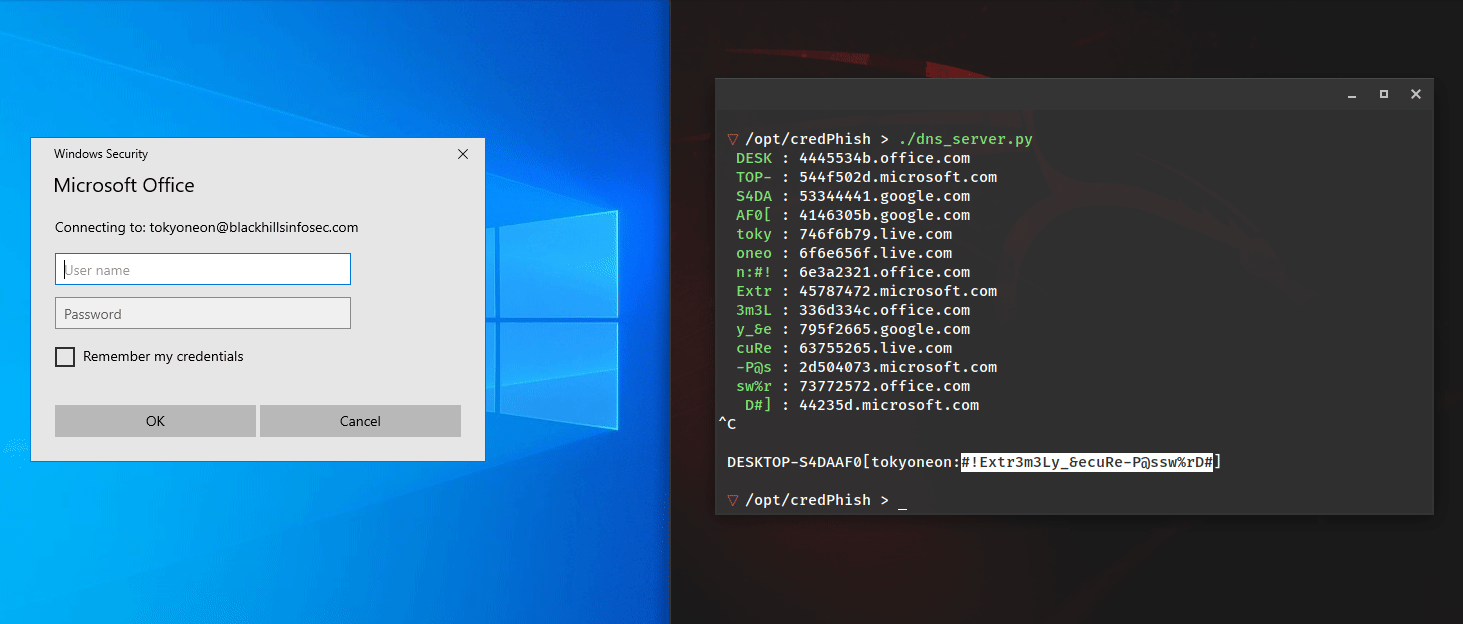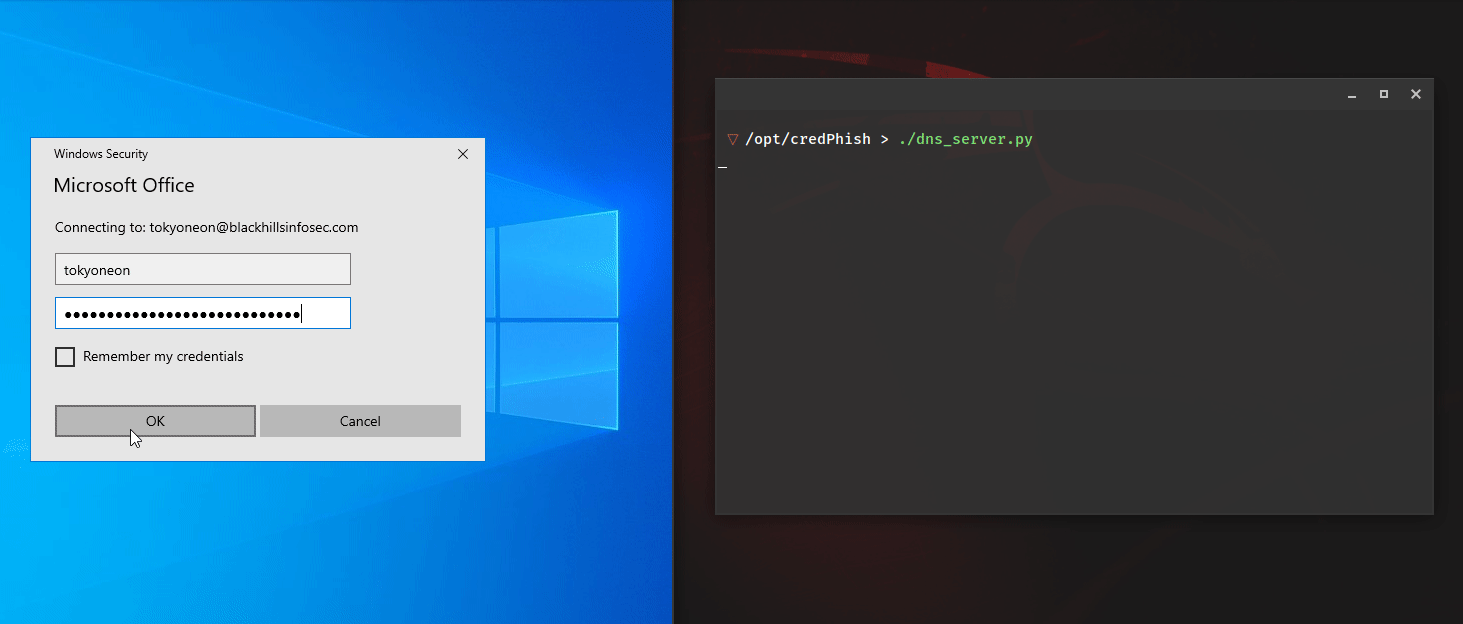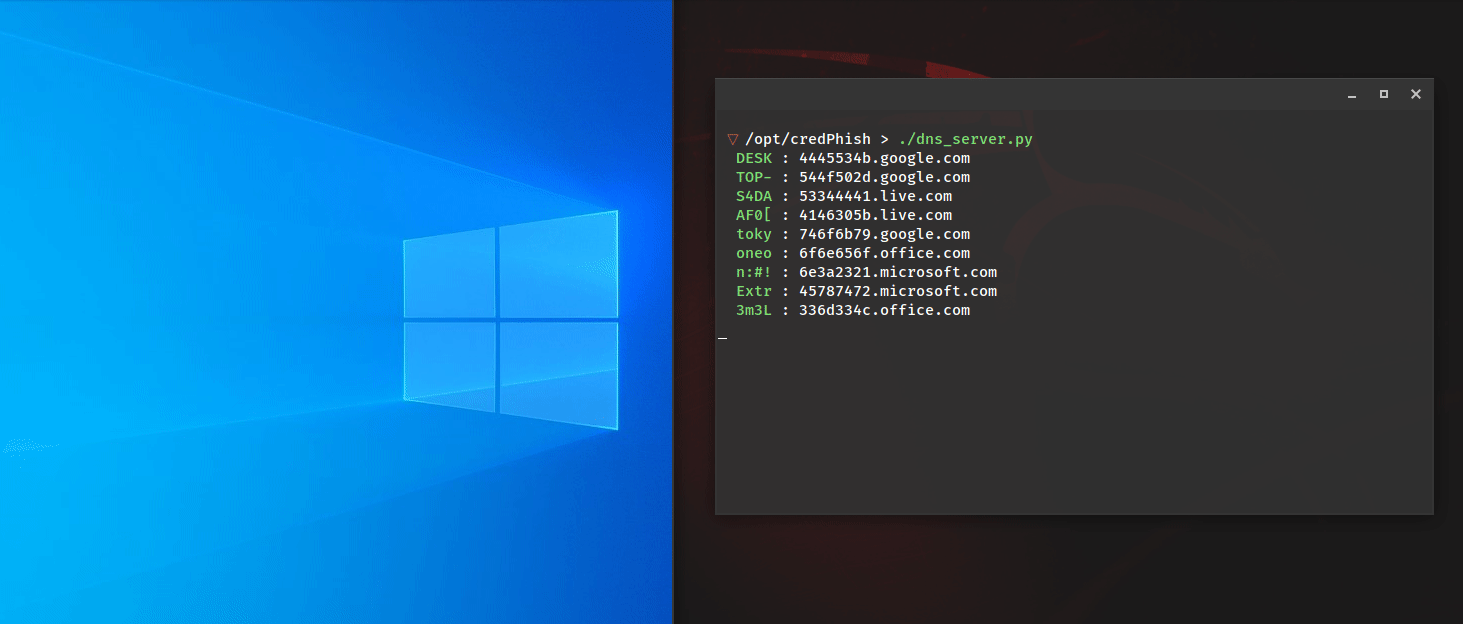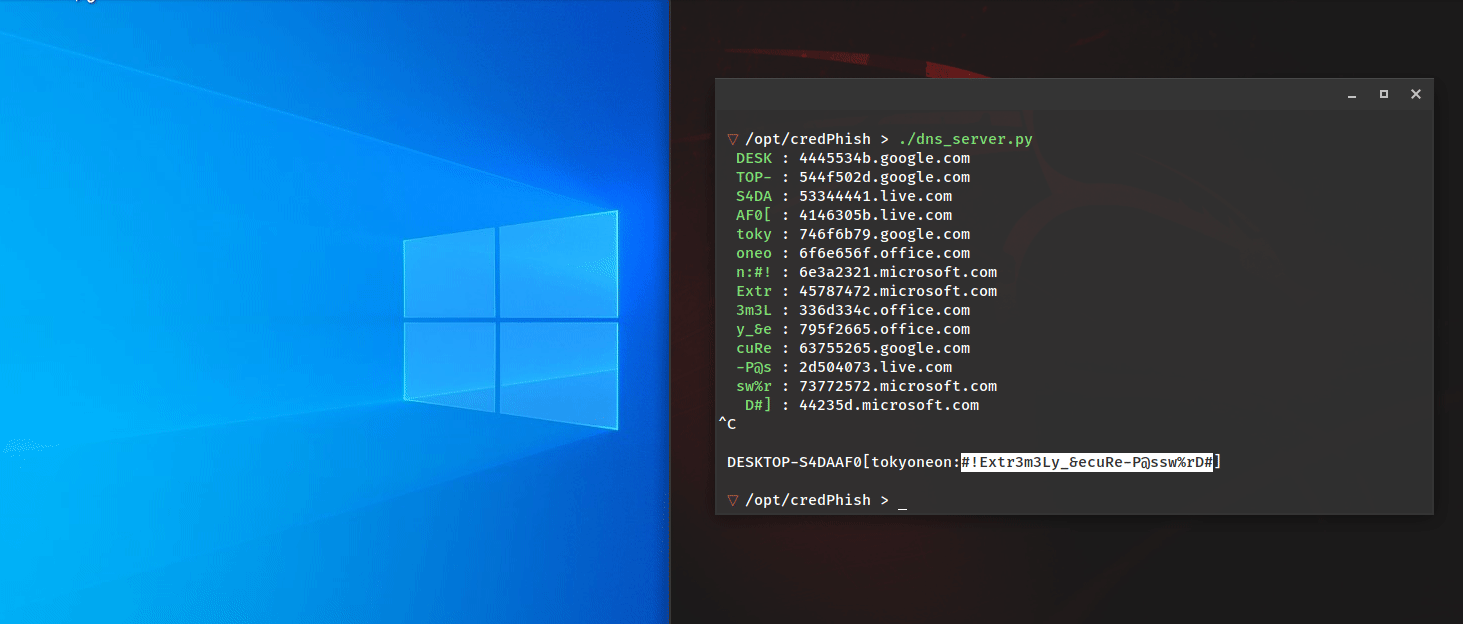
tokyoneon // Spoofing credential prompts is an effective privilege escalation and lateral movement technique. It’s not uncommon to experience seemingly random password prompts for Outlook, VPNs, and various other authentication […]

Why are companies still recommending an 8-character password minimum? Passwords are some of the easiest targets for attackers, yet companies still allow weak passwords in their environment. Multiple service providers recommend […]
Podcast: Play in new window | Download
Subscribe: Apple Podcasts | Spotify | Amazon Music | RSS

Michael Allen // Every year around the holidays I end up having a conversation with at least one friend or family member about the importance of choosing unique passwords for […]
Why are companies still recommending an 8-character password minimum? Passwords are some of the easiest targets for attackers, yet companies still allow weak passwords in their environment. Multiple service providers recommend […]
Podcast: Play in new window | Download
Subscribe: Apple Podcasts | Spotify | Amazon Music | RSS

Darin Roberts // “Why do you recommend a 15-character password policy when (name your favorite policy here) recommends only 8-character minimum passwords?” I have had this question posed to me […]

Carrie Roberts // *Guest Blog You have a password hash you would like to crack for a password that contains an Umlaut. You know, the two dots over a letter […]

Sally Vandeven// TL;DR – Passwords stored using reversible encryption, even if they are VERY LONG, can be trivially reversed by an attacker. Password cracking is quite enjoyable. It is very satisfying […]