Satellite Hacking
by Austin Kaiser // Intern

Hacking a satellite is not a new thing. Satellites have been around since 1957. The first satellite launched was called Sputnik 1 and was launched by the Soviet Union. It was a simple machine that sat in space at LEO (Low Earth Orbit). The only thing it could do was send radio signals back to the ground stations they set up. After three weeks, the thing died. But this was just the beginning.
It did not take long for satellites to advance. Just two years later, the first successful weather satellite launched from the US, providing the first television images of weather patterns. Two years after this, the first active communications satellite was created and was known as the Telstar 1. This satellite could send pictures, relay television, handle telephone calls, and fax signals. The next giant milestone for satellites was the 1993 launch of the Iridium satellite constellation. This was the first satellite phone network. The final milestone for satellites was the introduction of broadband internet services. This was done in 2005 by Hughes Space and Communications Company and marked the beginning of commercial satellite-based internet services.
Satellite technology is not stopping here either. One big advancement in the security realm of things is quantum communication. This technology uses quantum key distribution (QKD), which uses quantum mechanics to securely distribute encryption keys. Satellites that have QKD will send entangled photon pairs to the ground station, where they are received and measured to create a secret key between the two.
As of this writing, there is a working theorem known as the Quantum No-Cloning Theorem that says that it is impossible to clone quantum states. Hypothetically, this makes the key shared impossible to decode. Another new technology that is in the works is space-based solar power (SBSP). This involves the collection of solar energy in space that is then transmitted back to Earth with microwave or laser beams. (Crazy to think how we could be getting energy in the future from microwave beams.)
With all this talk about the history and future of satellites, what about the security of their systems? The very first impactful hack on a satellite was done on the British Sky Broadcasting’s satellite system. It was an impressive feat that combined a plethora of different techniques to avoid detection.
One of the methods they used was the use of backdoors. The attackers exploited systems that had low security and used backdoors to keep access and control over internal networks without detection. To continue to avoid being discovered, custom malware was used to bypass common antivirus software and intrusion detection systems. Once the attackers were in this deep, they deployed packet sniffers to pick up on data being sent through the network. They captured vital information such as passwords and other sensitive information.
To top off this attack, the attackers used multiple proxy chains to mask their identity and made it impossible to tell who was responsible for this attack. This successful attack caused data theft, operational disruption, and financial costs. Think about how long they could have been “sniffing” data on the network and just how much information they were able to gather from this attack.
How about a more recent attack? In 2022, Starlink services were offered to Ukraine to aid them in their war. Russia was not a huge fan of this, so, in response, they started lodging an attack on the Starlink network. The goal was to jam the network so that it was unable to offer internet services to the Ukrainian government. This worked briefly, but Elon Musk is known for hiring the best of the best to work for him. His resilience team proved more than capable of handling the attack. They quickly deployed software updates that enhanced the satellite’s resistance to jamming and further hacks. Because of the rapid countermeasures taken, the network did not stay down for long.
Are all attacks bad? The short answer is no. A fantastic example of an ethical attack or vulnerability discovery was created and successfully deployed by Lennert Wouters. Wouters is a security researcher at SpaceX. His job is to find vulnerabilities and highlight solutions to avoid them being executed by potential hackers. Within the cyber world, this is known as white-hat hacking, or the practice of ethical hacking performed by experts to find and fix vulnerabilities in systems.
Here is how it worked. Wouters created a custom modchip, which is a small device used to alter or bypass the standard behavior of hardware. Using this modchip, Wouters executed code on a terminal using a technique called voltage glitching. This involves manipulating the electrical signals to the chip, causing it to behave unexpectedly and bypass security measures. The Starlink terminals use a secure boot process to ensure that only authorized firmware can be used.
Unfortunately, this process can be disrupted by using the voltage glitching vulnerability. Once he discovered this, Wouters gained root access (the highest level of authority to a computer). Once he had this access, he could intercept or manipulate data sent or transmitted on this satellite. Thankfully, he was working for SpaceX and he disclosed the vulnerability, for which he received an award. SpaceX acknowledged the vulnerability and began working on solutions to it.
With all these attacks having happened, what effort is being made to stop further attacks of a similar or potentially worse manner from occurring? Sadly, there are a lot of engineers and developers who think they are safe using obscurity as a method of protection. In a post called “How Hackers Can Hijack a Satellite,” it talks about Willbold and five colleagues surveying 19 different engineers on their 17 different models of satellites. 3 out of 17 had no protection used to stop attackers from gaining access, and 5 of the 17 were unsure or declined to comment if they had some sort of defense on their satellite. Nearly half of the satellites deployed by these engineers had no protection set up or declined to comment on this. It is fair to say that satellite security seems to be a big problem.

Antisyphon Training has a course called Introduction to Cybersecurity in Space Systems (ICSS) with Tim Fowler that shows how to hack satellites in space using a virtual environment. This course contained within a virtual machine (VM) is a virtual simulation of an environment holding satellites and ground stations. It covers information on satellites, ground stations, attacks on satellites, and much more. My favorite part of the course involves attacking and taking control of a satellite. To understand how to do this, we must lay out basic information for you to know what is going on.
A very important piece of the satellite world is a ground station. What is a ground station? A ground station is a facility equipped with systems that communicate with satellites for data transmission and reception. For an attacker to communicate with these satellites, they must have a ground station.
To have a functioning ground station, you must have the following components: An antenna system to receive and send signals to and from the satellite. You need radio frequency equipment to amplify the incoming signals without adding noise. A power amplifier to boost the signal you are sending to the satellite. Modems are needed to modulate and demodulate the signals for communication. A software-defined radio is necessary to allow flexible handling of frequencies and signal types. Tracking software to calculate the satellite’s position, allowing you to know when the satellite is within range, as well as rotating the antenna to follow the trajectory of the satellite in the sky. A power supply with a reliable flow of power is needed to keep the systems running while in use. Networking equipment such as routers and switches are needed for your internal network connectivity. The equipment will need to stay cool, so some sort of facility will house these devices while they work. These ground stations are not as expensive as you might think. As little as ten thousand dollars should do the job to get you set up.
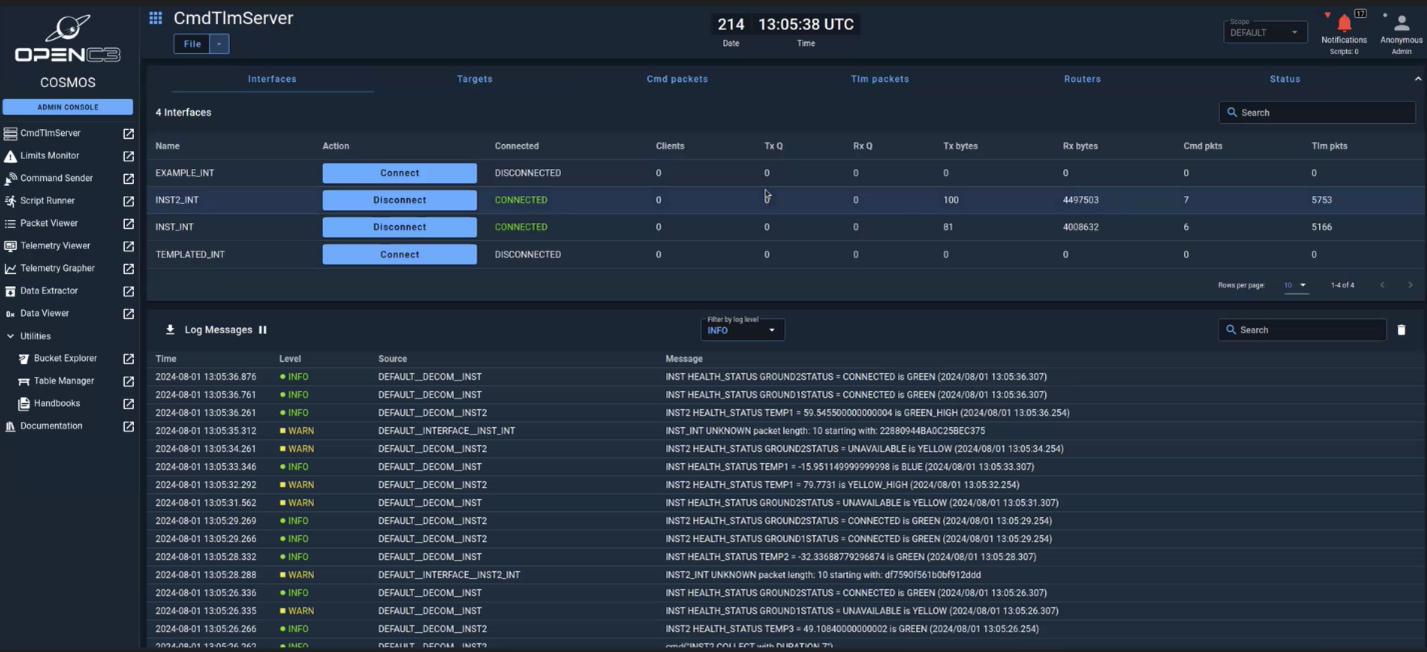
In our VM, we use a software known as “Command and Control Open-Source Mission Operations System,” or COSMOS, to simulate what a ground station would look like. In this simulation, you can think of COSMOS as the ground station that should send and receive data to the satellites we deploy. For our satellites, we will be creating containers based on NASA’s Core Flight Systems (cFS) and Hackstar. These will be the two satellites we are using for the simulation. Using this information, let’s dive into what attack we will be showing today.
A spoofing attack is a cyberattack where an attacker impersonates another device to gain access to data or systems. Within the satellite realm, a typical spoofing attack is tricking the satellite into thinking that your ground station is the ground station that it is supposed to be communicating with. In the course, the cFS satellite should be communicating with the COSMOS ground station. However, we are going to trick the cFS satellite into thinking that our attacker machine is COSMOS by sending it a packet that has the command to enable telemetry.
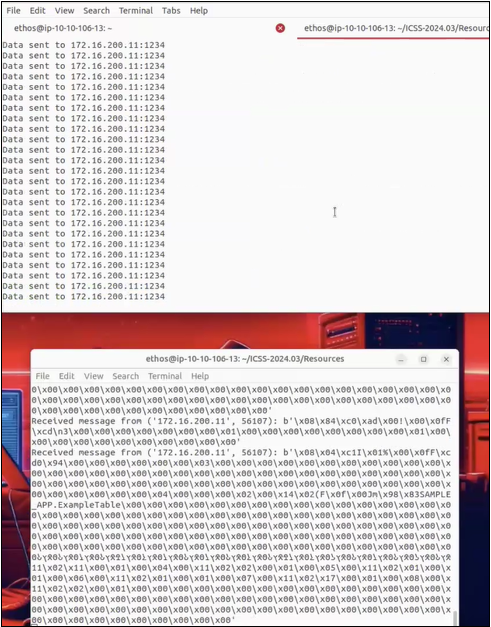
Telemetry is the collection and transmission of data from a device to a central system. In our case, this is the data that the cFS satellite sends back to COSMOS. The command to enable telemetry requires an IP address that specifies the location of where to send the data. In our Python script, we found which part of the command holds the IP address to send the information. We replaced this with our IP address, essentially telling the satellite to send the data it receives to our attacker machine!
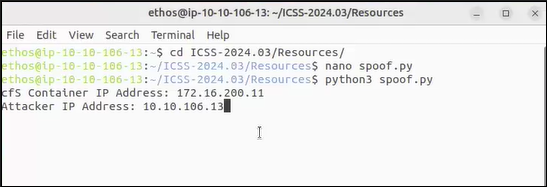
This successfully tricks the cFS satellite into sending all of the data it collects to our machine. All the while, the satellite is thinking nothing is wrong. In a real-world situation, this attack is best done when the satellite is moving out of contact with ground station A and about to come into contact with ground station B. At the point of it switching, we can trick it into thinking that we are ground station B, as it would be looking for who to send the data to next.
A jamming attack is a cyberattack where an attacker transmits junk signals that interfere with legitimate wireless signals. A very common name for this is a denial-of-service (DoS) attack. In the course, we create a Python script that sends packets having random amounts of A’s in them.
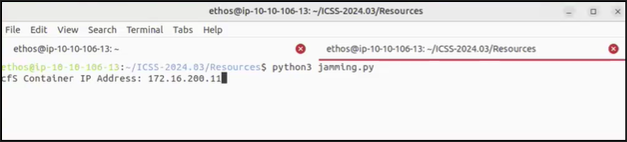
When the script starts, COSMOS cannot send a legitimate command due to all the packets we are sending. There is so much “noise” being sent to the cFS satellite that it is incapable of receiving anything anymore.
Let’s combine these attacks! In the ICSS course, this combined attack is called RF attack chaining. The goal with this is to lock out the COSMOS ground station and fully take control of the uplink and the downlink of the cFS satellite. The uplink is the ground station sending information to the satellite (sending information up to the satellite) and the downlink is the satellite sending information to the ground station (sending information down to the ground station). To start the chain attack, we are going to attack the cFS satellite with a spoof attack to hijack the downlink. That way, any information this satellite sends is now going to be sent to us. As soon as this is successful, we are going to start the jamming attack. This jamming attack is going to hijack the uplink. So much noise will be sent to this satellite that it will no longer be able to receive any commands to change what we have done. This locks out COSMOS from seeing and sending any data.
In a real-life situation, this can be a detrimental attack. If an attacker could perform these attacks on a satellite, it could do any of the following examples. Disrupt services that rely heavily on satellite communications — things like GPS, weather information, and data communications are all on the table. There would be safety risks with flights, ships, and vehicles that could cause accidents. The military and defense operations could be in trouble due to a blackout period where they are not able to see or hear anything. If there were a forest fire and people were tracking it using a satellite and that satellite were to be attacked at that time, there would be no way to track the damage or potential damage the fire could cause. There are so many situations that this sort of attack could escalate to.
Interested in learning more? Check out these classes:
Introduction to Cybersecurity in Space Systems (ICSS)
Introduction to Cybersecurity in Space Systems (ICSS): Hardware Edition

