Intro to Desktop Application Testing Methodology
This webcast was originally published on October 24, 2024.
In this video, experts delve into the intricacies of desktop application penetration testing methodologies. They discuss various techniques to thoroughly evaluate application security, including memory analysis, DLL hijacking, and network analysis. The conversation also highlights the importance of creating a comprehensive testing strategy and the value of documenting findings during the testing process.
- The webinar discussed a comprehensive approach to pen testing desktop applications, emphasizing the importance of understanding the application thoroughly before diving into complex reverse engineering tasks.
- The presenter advocates for a detailed scoping process during a pen test to ensure that all relevant components and potential vulnerabilities are within the scope of the test.
- The importance of reporting as you go was highlighted as a key methodology in pen testing, facilitating a seamless documentation process and ensuring thoroughness.
Highlights
Full Video
Transcript
Craig Vincent
Yeah. So who am I? Obviously, I guess I test a lot. I didn’t know that, but I do a lot of pen tests. I study computer science, computer security and math.
In college, that’s kind of how I got into infosec in terms of learning, security stuff from technical perspective. And they also kind of point us and they’re like, hey, there’s a thing called defcon.
There’s this, Linux distro with all these hacking tools on it kind of point us in the right direction for where to go for resources to learn on our own. when I graduated, I started working, pretty much right away as a software developer.
Didn’t really like writing software all that much. So I was like, well, I know this computer security stuff. Like, let me get good at that and try to get a job doing that. And initially I wanted to be, a malware analyst because, like, the whole stuxnet thing happened recently.
I think I read Countdown to Zero Day, like right when it came out. And I was like, man, that sounds really cool. I want to learn that. And so you learn by doing it.
So I, like, had my home lab and I was doing reverse engineering stuff. I think it was open security training info, or DOT info, was a website that had a lot of, like, reverse, engineering, binary analysis, webcasts, and kind of, like, trainings.
And it was all free and on YouTube. And so I went through all that and then I started doing, like, reverse mes and Crackmes and looking at some, like, older, like, malware samples. And I was like, okay, I’m getting okay at this.
And then I was like, I really don’t like this. I don’t want to do this anymore than I want to do software development. So I was like, I hadn’t really considered pen testing. I used to think that, like, those guys are boring.
They just run scanners and stuff and then write a report about it. And then I saw Security Weekly. There was this guy on there who had a pen test company, and he’s talking about pen test Puppy mills and how it doesn’t have to be like that, that.
And I was like, okay, let me try that. So it was back to square one. home lab, intentionally vulnerable VMs, like a damn vulnerable web app, like, just learning hacking skills, right?
So that led to me getting a security job doing red teaming. And then right after that, I came to Black Hills, and I’ve been here ever since.
Other things you can get me to not shut up about are golf, football, swimming. So if you ever want to hang out at the con or something to talk about stuff and get me to not shut up, those are all good starters.
So as Jason mentioned, this is not a, a vuln research, like zero day exploit development, like reverse engineering talk, right?
Because that’s what I. That was my initial thing. I was like, they’re like, hey, Craig, we got this test. It’s a desktop application. And I was like, okay, well, what’s the expectation there, right? And initially I kind of panicked because I was like thinking.
I was like, oh, yeah. I mean, I was a developer. I’ve done some reverse engineering, I’ve done network pen testing, I’ve done web apps. I’ve done all these different things. So I think I had the skill sets. But I was like, where do I even start? I don’t want to end up sitting in front of a debugger for a week and them expecting me to find a zero day and then not have anything.
Right. And so after I kind of like stopped panicking, I started looking around. I was like, okay, there’s got to be a methodology out there. There’s got to be a kind of uniform, kind of like, thoughtful way to go about doing this.
And I found that there wasn’t a whole lot. Like, I found like a Reddit post that mentioned some things that you might try. OWASP had like a little bit of a checklist. And so I kind of use that as like a starting point and then kind of built my own methodology.
And I don’t know if this is like a more recent thing, but I went from not doing any of these tests to I think I’ve done like three or four in the last year and a half. And I haven’t done bug bounty in a while.
But I looking into this because I wanted to have a sample, to hack on for the slides because I can’t show you screenshots of customer stuff. I was just searched, like bug bounty programs that are public, that have desktop applications in scope, and there was a bunch.
So it looks like it’s becoming more and more common. so this is kind of just like my high level, like how I approach, looking at an application from a security perspective without going too in the weeds with all like the, disassembly, reverse engineering, all the gnarly complicated stuff.
There’s a lot of other stuff that you can do that you probably should do before you get to that point. So that’s mostly what we’re going to be talking about here.
I want to kind of, I want to make the point that this is like a pen test methodology. So I like to compare it to web app pen testing versus bug bounties, where a bug bounty is more of like a proof of concept or get out type situation.
Where a pen test is more about coverage and being thorough and you’re going to report things that they may not care about in a bug bounty. Right. So this is kind of the same thing for desktop applications where this is not like pwn to own.
Looking for a zero day like proof of concept, like POC or gtfo. Right. This is like a methodology, like check all the things like be thorough.
just want to make that clear. So the first thing you’re going to do is you’re going to be scoping. and this is going to be usually during your ahead of your rules of engagement or during your rules of engagement, you’re meeting with the customer, you’re asking them, okay, like what is it that I’m testing?
And I always like to ask for a more inclusive scope. I like to have more stuff included. And some people might want to push back on that.
They’re like, no, we just want you to test the application. But it’s like, well the application talks to these servers and it uses APIs and does all this other stuff. Like can we include that in the scope? And that’s not just me being like a greedy hacker man.
Like I want to have more things to hack on. that’s a kind of a. Okay, yeah, maybe these things were tested on like your regular network pen test or as part of like, maybe it’s like an API as part of your web app pen test.
But like, what if your desktop application has used it in a different way? Maybe there’s more coverage to be added. There’s a different context. so I like to have as much stuff included as possible.
So like APIs, other associated infrastructure, I try to get them to provide source code if possible. Not that necessarily I’m going to like dive right in the source code immediately. But having it there available as a reference is helpful.
And the other thing I also do when I’m doing the ROE and asking about scoping is I ask them for what their areas of interest are, what are the things in the application that they’re worried about, what’s the new stuff, where are the skeletons sitting?
A lot of times they know and a lot of times they’ll want you to go find that. and they can kind of point you in the right direction.
And pretty much every test that I do, for the most part, I do some level of reconnaissance of some kind just to give myself more information. and for desktop applications, first thing I want to start is documentation.
either I’m going to ask for that during the ROE too. Like, hey, give me whatever docs you got, I need that. If they don’t give that to me or they don’t, or they forget or whatever, I can go look.
And whatever’s out there publicly available, I’ll pull that down and I’ll read that. And reading the documentation is really helpful because it’ll basically tell you interesting features and stuff in the application that you might want to go attack.
So, like, oh, yeah, it runs a service on this port that does this and it. Or you can import a file and have it processed to do this. And it just, it’ll tell you the information, the interesting stuff in the app that you want to look at.
And a lot of times these are, these are at least my experience from doing this. These are mostly commercial applications that are well known that people use. Right. That’s why they’re having pain to have it tested.
So a lot of times they’ll have had previously, disclosed vulnerabilities. So that could be, maybe just. They do their own bolt, like you, just like Microsoft, Cisco, they’ll post their own things.
Hey, yeah, we had this vulnerability affects this, this, this. there’s CVEs out there and stuff that get published. there’s proof of concept exploits, on exploit, DB and GitHub and other places.
So you can go and look and see. And the idea is you’re seeing, okay, like, this thing has had vulnerabilities in it before. And one thing you want to check is like, okay, is that a common theme?
Like, can I look for that same kind of vulnerability in other parts of the application? Because they may have fixed it here, maybe it exists somewhere else. another thing that occasionally happens is that, they have a vulnerability that gets disclosed and they patch it and the patch is not completely effective.
Like, there might be a way to get around the patch. And a lot of times the researchers who find these things will go back and look and double check and see if there’s another way they can bypass the fix. but that’s something that you can always look at, hey, this vulnerability.
And then if it’s, especially if it’s like open source, you can look, say, hey, what is the change that they made? And then is it. Can I think of a way to get around that and then basically reopen this existing vulnerability?
you’re going to want to look in a lot of, a lot of times these big projects will have, they’ll have GitHub repos like GitHub, accounts and they’ll have maybe not the entire source code but they might have like dev tools they use, they might have other things or components of the application that are, that are open source that they just have out there.
And you can go look through those for secrets, you can look for information about how the application works. another interesting thing, I haven’t actually found any vulnerabilities doing this in an actual application I was testing yet, but it’s something that I’m recently incorporated is a lot of times they’ll have the fork a repo from an existing project, like a bigger, more popular project and they’ll like fork it to do their own extensions and things like that.
Well when they do that all the other they don’t necessarily always like merge the other stuff that gets added to that main repo into their forked repository. Right? So it’s like a separate, totally separate thing.
So if you go look at the thing they forked and look at its updates and commits and look for recent security issues in that. Well if it’s a newer commit in there and they fixed like a security bug, you can go check and see, well, does this thing exist in my customers fork that might be in their application?
And so that’s just being lazy really. I mean just like letting other people find stuff for you that you can use against your target. look for secrets in there like a lot of times like old commits, like if it gets committed like API keys or creds or stuff like that, those kind of stay in your git repo, even if you write over it.
So you want to look for that stuff. there’s other places besides GitHub, like BitBucket, Sourceforge, there’s other places your customer might be hosting this stuff. So just Google dorp that stuff and go find as much as you can.
Okay, so you’ve done a little bit of research. You’ve got your docs, you’ve read through the docs, you’ve done all this stuff. Now you have the application. What’s the first thing you want to do? The first thing I like to do is figure out what the application is doing on my host.
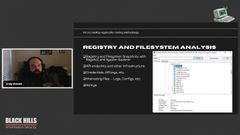
So I have my every, every new test I do starts With a fresh vm. So I spin up my Windows machine and I download the application. And what I’m going to do is I’m going to take, a registry and file system snapshot of this thing before I install and run the application.
And I do that with. I think System Explorer is better. Reg Shot is the older tool that I’ve used. I’ve used them both recently. they work, but basically they’re taking a snapshot shot of the file system and the Registry just of the machine.
So you take one snapshot, then you install the program and you run it and you start doing stuff with it. And then once you feel like you’ve sufficiently sussed out all the functionality of the application and everything that it might do, you go ahead and you take another snapshot and then you can compare those and that will show you, all the stuff that has changed on your test machine, like files, registry key, stuff like that.
And then you can go look at those for interesting things about the application. So you’re looking for any interesting files that are put on there. If it’s got logs or config files, you want to go look at those.
a lot of times this will open up and expose additional attack Surface. If they’ve got like Registry keys for servers they’re talking to, they might, I’ve seen, I’ve seen keys and creds in Registry keys too.
So just interesting stuff that you might be able to leverage later. you’ll look at that and then of course all the application, files, where those are now.
and so you can, I like to take all those off, put them on Linux machine and run strings on them just to get useful, ASCII strings out of these files, see if there’s anything interesting in there.
And that gives you a pretty good idea of like what the, what the footprint of the application is on your, on your machine as a starting point.
then you can look at the actual binaries and say, okay, like what, how’d they make this thing? Like, what language is this? you can use CFF Explorer Detectives. There’s lots of other tools that will, that you can use to point at binaries and they’ll tell you all kinds of interesting stuff.
I think, I think Gator does it automatically. but you look at these things, say, okay, like, get more information about, like what’s it, what’s it written? And, and if it’s written in C Sharp or Java, decompiling these to not necessarily the original source code, but like readable source code equivalent, is pretty straightforward using tools like iLspy, p.
J.D. the tools that I’ve got listed over here. I haven’t actually used any of the Java ones recently. I think the last time I’ve done this with a Java application was like a while ago and I think I used the old Jad tool.
But there’s apparently newer ones that I came across when I was doing some research for this. Just know that if it’s C Sharp or Java, then you can probably get a pretty good representation of the original source, in a pretty straightforward way.
So that’s helpful because then you can actually walk through the source code then you can look at other things.
So there’s a lot of these like binary protections that these compilers and systems have kind of built to help developers make code that’s more difficult to exploit.
So like your address based layout randomization, your safe seh, your depth stuff like your control flow guard, these are all things that you can like. They’re basically compiler options that you can throw on there to make your application harder to hack.
So you can check these with Bruinscope and with PE Security. And I’m going to have links at the end of this for all these things that I’m mentioning because I couldn’t figure out how to make footnotes work in PowerPoint.
So I just have a link slide with a bunch of stuff on it. So you check that out at the end. but Binscope requires debugging symbols. That’s something they’ll ask for from the customer if they can get that when I’m doing the roe otherwise it won’t work.
But you can check things with PE Security as well and it’ll just basically it’ll go through all of your all your binaries and check for these different options.
and this is Canva, this is. I mentioned the bug bounty program. I just went, I just picked one to. I didn’t hack it or anything. I just kind of walked through this methodology. This is not anything they would care about. So it’s not like a irresponsible disclosure when I’m doing this like this.
So please don’t get angry. Canva, you can check application signing with Sysinternal Suite has got a tool called SigCheck.
Basically it basically checks the code signing of the, this stuff. and that’s just an integrity check on the miner itself to make sure that it hasn’t been like modified or dorked up by any malicious actors.
Right? It’s the stuff that the publisher developer made, process identification.
So I. You can use Task Manager or. I like procmon. Procmon is pretty sweet. We’re going to talk more about procmon when we get to DLL hijacking. but yeah, you just look in here in Proclamation, you can look at all the processes, you can look at the parent processes, like where it got spawned from, just to get an idea of what processes your actual application is running and spawning and doing.
I did want to mention, this was something that was interesting.
when I was looking at the files for this thing, going through my, the files I got added to the system, they had like a licensing thing for Electron.
And so just looking at that stuff kind of you like say, okay, well what’s Electron? If you Google what’s an Electron app? And you’re going to find out that it’s all this like web stuff kind of crammed into, a browser in a desktop application.
It’s kind of like a really simplified explanation of it. But basically just knowing that, like, going through this stuff and figuring out what technology is made with gives you a better idea of like, different ways you can go about attacking it.
I think I forgot to mention that earlier. I just want to go back and touch that, memory analysis. There’s some more complicated things you can do with this. But my favorite quick and dirty thing to do is just take your application process in Task Manager, right click it and create a dump file and then you can run strings on that and you can find a lot of interesting stuff.
Because this thing will have data in memory that is potentially sensitive. Would have like API keys, creds, private, cryptographic keys that you might be able to then leverage against other stuff that hopefully you’ve had included in the scope and say, okay, this is an exposure here, because this is all one system, it’s not just this application.
So, looking for sensitive stuff stored in memory at runtime. that’s the quick and dirty way to do that. here’s another one, DLL hijacking.
this is one that’s kind of like. Well, as a software developer, you don’t control the endpoint. So there’s this DLL hijacking thing where basically a malicious actor gets your application to load their DLL instead of one of your DLLs.
And so it’s based on the search order for how DLLs get loaded. And it starts with like the directory where the app was loaded from. Then it goes, looks like the system directory and then like I think another directory and then it looks like at your path variable.
I don’t remember off the top of my head, but it’s basically that’s where it goes to look for these, these DLLs. And if you can write a DLL of the same name to somewhere in a higher priority in the search order, then you can potentially get it to load and execute your dll.
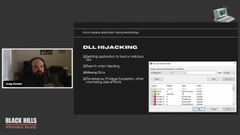
the one that I look for the most, that I think developers actually care about the most or should care about, is missing dll. So if it’s looking for a DLL that doesn’t exist, and you can write to there, that’s an opportunity to do this kind of thing.
Use Process Monitor to do this. If you look here, these two green checkboxes in this filter are just the things that I added. You’re looking for a result where the name is not found and the path ends the DLL.
So this is basically like all the DLLs that it can’t find. And you apply that filter and you can look at all the proclamation has everything. So you just look for your target processes that are looking for DLs that it can’t find.
And what you do there is you just put your malicious DL in there and it gets loaded and run. and this has applications for attackers and but because they can establish persistence, right?
So let’s say you get C2 on an endpoint and the person restarts their computer. Well, you just lost that, right? But if you have this, if you have DLL hijacking on like a commonly known software, and you’re pretty sure they’re running it and you find it on there, then you can load this malicious dll.
So the next time their computer boots up and this application is run, your DLL gets loaded, Boom, you’ve got C2 again. it works for privilege escalation occasionally, depending on the permission.
So when you do this, and your DLL gets loaded, you’re now got code execution in the privileged context of the process that loaded it. So if you’ve got like, for some reason a highly privileged process or software that loads your dll, you’re now running with those privileges.
And that could be a higher privilege level than what you would have as like a normal user. Right? Other, interesting side effects.
I was kind of testing a EDR that will remain unnamed. And so one of the things that I was testing is like, okay, what C2 can I get out? So I had like cobalt strike beacons and I had a few of those that were work that were going back up and they were working fine.
And it was also affected by DLL hijacking. And so it had the remote kind of quarantine feature. Right. So you basically say, hey, we detected malware on this computer, let’s isolate it.
Well, I went ahead and did that on my test machine using their portal and I lost all my beacons. All the ones, the regular ones kind of went away except for the one that was the DL hijacking beacon because it was actually running in their EDR process and they weren’t isolating that because they have to maintain that control over the endpoint to continue doing their EDR stuff.
That’s just another weird side effects of things that can happen with this that as a developer you might care about.
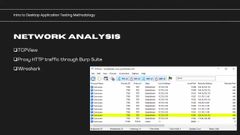
network analysis. just use TCP view and see what it’s talking to. If you look here, canva talks to a bunch of these web servers, least they look like web servers based on the ports.
And then it looks like it opens and listens on this port. And that just gives you an idea of like the network communications the application is going through. I like to always proxy web, traffic through Burp Suite because why wouldn’t you.
That gives you all the tools that you would do for your normal kind of web application pen test methodology against these other endpoints and other infrastructure. Right. for other protocols and other traffic.
You can use wireshark, to kind of just capture all that and then go through it. this is kind of like, this is very much generic.
This is like a choose your adventure is every application is different. but in this instance, like so this, this port that it’s listening on, this is something you’ll want to fuzz. Right. And so we’ll talk about fuzzing.
There’s lots of. Basically fuzzing is you’re taking a service that is listening or it’s some other way you can input data to this application and you’re feeding it a bunch of stuff, garbage, for lack of better terms.
Some of it’s, it’s more, it’s more calculated than that. But you’re feeding it stuff until it breaks. And that’s the long and short of how you start to find vulnerabilities in applications. there’s a bunch of fuzzers out there for network stuff.
These are just a few examples. I haven’t used all of them. I really want to look at Cluster Fuzz, because that’s the one that Google does that they use to find like, like thousands of bugs in Chrome themselves.
these are just some examples of buzzers that you can do for these network applications. So if you got a desktop application that’s opening a port and listening one, hundred percent want to fuzz it.
Yeah, I got through that really quick. That’s, 25 minutes. here’s the links. Deb is going to have the slides in a PDF format, so you can have all of these and I guess we can do questions.
Jason.
Jason Blanchard
Hey, Craig.
Craig Vincent
I kind of flew through that, but hopefully, yeah, hopefully I got it all.
Jason Blanchard
Well, that just gives us more time for Q and A. Yep. someone said be aware that PE Studio is now Pay to Play.
Craig Vincent
Did not know that.
Tom Smith
Yeah.
Jason Blanchard
All right. so if you have any questions about some of the stuff that Craig just covered, feel free to ask inside the, can someone, ask if you can put the links back up?
you can also download the slides here, through Zoom. So if you go to Resources, is it in Zoom? Ryan?
Craig Vincent
Deb?
Jason Blanchard
Ryan?
Deb Wigley
Hmm? We m. Can put it in Zoom.
Jason Blanchard
Okay. It’s also available in Discord and the Slides Resources channel. Okay, Craig, here’s your first question. Are you ready?
Craig Vincent
I think so.
Jason Blanchard
All right. How far will you take a desktop test? When do you consider a test completed?
Craig Vincent
when I run out of time.
Jason Blanchard
Okay.
Craig Vincent
That’s the. I mean, that’s the. That’s like the cheeky answer, but it’s one of those things where it’s like, I. These are usually time box. I get a week, and then I get as much as I. That’s why, that’s why I want to do all this stuff before I start reverse engineering and doing all that, like, gnarly stuff.
Because I don’t want to sit in front of a debugger for a week and not find anything and be like, oh, I looked. Here’s my one page report. Like, I’m gonna do all this stuff first to get more familiar with the application before I start going, stepping through the source code, debugging all that stuff.
So just. And then I do that until I run out of time.
Jason Blanchard
Someone wanted to know more about the TCP view and what it does exactly.
Craig Vincent
it just looks at network traffic coming in and out of your device. That’s a. That’s a tool from System Internals Suite. it does TCP, UDP, IPv4, IPv6.
It just tracks connections. It’s like a really, really cool. Net stat.
Jason Blanchard
Someone wanted to know if you were getting started in this, would you start with Python C Assembly or reverse Engineering?
Craig Vincent
I would say, honestly, I don’t really know. I would. I just know what I did, obviously I studied, I knew how to code and we did some assembly in college and then the open security training.
Let me actually get that link for you. I’m going to look that up here because I got Nerd Snipe. That’s where I learned a lot of this stuff from. And it’s a little bit older now, this is probably 10 years ago, but they had some really good courses.
There’s a guy, Xeno, Kova taught some of them and they had yeah, it’s opensecuritytraining.info and it looks like it’s all still off there.
They had the Introduction to Assembly stuff. They had Introduction to Reverse Engineering. the course they’ve got called Life of Binaries is really cool because it actually shows you how applications, are put together and work and run.
I would recommend those. there’s probably something out of better, but that’s just the stuff that I used and I thought it was very, very good. but yeah, definitely you want to know assembly.
If you’re gonna actually get into the reverse engineering and like, if you’re actually gonna try to write a proof of concept exploit, you kind of need to know that, I don’t typically get that far during a pen test if it’s only like a week.
But that would be the next step, someone said.
Jason Blanchard
Is TCP view like Wireshark?
Craig Vincent
no, not in that it captures packets and stuff. It just kind of tracks connections. It’s kind of a logger almost. Whereas Wireshark will actually capture the traffic for you.
Jason Blanchard
Okay, so we got a bunch of questions coming in. Keep the questions coming in because when a webcast isn’t the full 60 minutes, we have a lot of time for Q and A and for people who are intro and getting started in this, this is like your opportunity to ask someone who does this all the time whatever questions you have.
Craig Vincent
So definitely question I’m so I’m gonna, I’m gonna stop sharing so I can actually see the zoom again and see the chat scrolling by a little bit.
Deb Wigley
yeah, someone, asked are most desktop apps today electron based? And does this complicate the testing methodology?
Craig Vincent
I don’t know. My sample size is not large enough to give an authoritative answer on that. But I understand that it’s a pretty popular technology.
Jason Blanchard
Do you like process hacker VirusTotal marked it as malicious binary?
Craig Vincent
I have heard of that. I’ve not used it.
Jason Blanchard
I. I have a Jason Plantry question for you that I ask every single tester that comes on here. All right, so it’s going to be a bit personal. Are you ready?
Craig Vincent
Yes.
Deb Wigley
Save that to the end or you want to put in there now?
Jason Blanchard
Okay, I want to go now. when you’re doing a test as a pen tester, when you’re doing a test and you’re unable to find something or find a way in, do you start to question your own skills and abilities or do you feel like this product or service is secure?
Craig Vincent
not anymore. I don’t really question myself. I, just make sure I document everything that I’m trying to do. You can tell pretty early on now with the experience that I’ve had is like, I can.
It’s more the latter. It’s like this thing looks like it’s pretty locked down and you can tell pretty quick that none of the stuff that I’m trying to do is working. So it’s time to document everything because they’ve got a lot of stuff, done correctly and that’s good for them.
And it’s frustrating sometimes, but it’s not like a bad thing. It’s not. It doesn’t freak me out anymore like it used to.
Jason Blanchard
Okay, so there was a period of time it freaked you out if you weren’t able to find something?
Craig Vincent
Yeah, I mean, early on when I first started doing this stuff, it was kind of like, man, do I just suck or, like, are they good? Like, I don’t know. But now I’ve done it enough that like, I can pretty much tell that it’s that they’re good and I don’t suck.
So, yeah.
Deb Wigley
Nice.
Jason Blanchard
Cool. Deb, do you have another question?
Deb Wigley
Yes, I do. I sure do. what method do you use to proxy traffic for desktop apps that don’t honor the system proxy settings?
Craig Vincent
That’s a good question. I’ve not encountered that. the worst thing I’ve encountered is certificate pending, which is a pain in the ass because then you have to, like, give it to unpin so you can actually intercept the traffic.
I’ve not encountered that in terms of not, being able to capture, at least not that I’m aware of. I’ve been able to intercept HTV traffic, that I can see, like, TCP view.
I’ve not had an issue with that. So I, I don’t know. I don’t, I don’t know how. If I could see that it’s like talking out a web server and like in TCP view and then I actually can’t intercept that. Then, then you’re talking about.
I would have to start Googling. Like there’s got to be a way, especially because I’m using a vm, there’s got to be a way to hook that. but yeah, I would have to figure that out. That’s a good question. I don’t know.
If somebody does know, I’d love to hear. If I do run into that, I’m going to, I’m going to want to not have to figure it out on my own.
Jason Blanchard
we had a question from Discord. Do you have an assessment playbook that you refer to when you do pentest?
Craig Vincent
yeah, I mean that’s kind of the methodology. This is kind of like if you. My webcast methodology, webcast that I did a while ago, is kind of like me walking through my playbook.
that’s kind of like what this was for desktop testing. It’s, it’s basically I like to have checklists in an order of operations and kind of like a well formed methodology for how I go about it.
So that’s kind of like what this was up until the universe engineering stuff. Because I don’t want to get into that right now. That’s too complicated for a webcast.
Jason Blanchard
I’m dropping the link, to your web application penetration test methodology into the.
Craig Vincent
Yeah, that was a very similar talk that was kind of a quick and dirty like I, I probably tried to do too much in that one. That’s why I try to do not as much in this one. But that was very much like everything that I do on a web app pen test, like in terms of coverage all in like an hour.
Deb Wigley
another question from Discord. Could you please elaborate on compromising upstream repos so that stuff is pwned on their next build?
Craig Vincent
Right. So you’re not compromising upstream repo. You’re looking at the upstream repo for vulnerabilities that have been fixed that are not applied to your targets fork, if that makes sense.
So like they’ve, they’ve forked right here and so they’re over here and the other repo is going up this way and they find a security vault up here and they fix it. If that’s not been done over here, then it’s probably affected, if that makes sense.
And I’m not actually found anything using that technique, but it’s something that I’ve started looking for because I sure it exists because a lot of these places are forking other existing projects to incorporate in there.
that’s a funny gif to incorporate in their, products.
Jason Blanchard
Yeah, this is a programming thing. Is Tom here? Tom, can you hear me? This is not like a seance. Tom.
Deb Wigley
Tom. Tom Smith. Tom Smith. Tom.
Jason Blanchard
Tom Smith. Do you. Is your microphone working? Like, can you talk in the webcast? Not in the chat. Not in the chat. Our side chat.
You’re talking now. No, you’re not. All right, so we gotta get that fixed.
Craig Vincent
I did see a question somebody asked me about how much I Google. I can’t scroll up. But yeah, I Google a lot. And it’s not just because as a last resort, it’s kind of a.
there’s constantly new techniques and new tools and stuff coming out. Like I found new stuff when I was doing research for this since the last time I did of these tests. So, that’s how I found about the, the Google fuzzer that they’ve got that I really want to play with.
But yeah, I, I Google a lot. An obscene amount.
Jason Blanchard
Hey, Ryan, can you tell if. Is Tom just watching the webcast or is he actually here in the webcast? I, I think he’s just watching the web.
Okay, does anyone else hear Tom?
Deb Wigley
I do not hear Tom.
Jason Blanchard
All right. it depends. Have you seen any interesting vulnerabilities that show up from cross compiling frameworks like.netmaui that show up in desktop and mobile apps?
Craig Vincent
Not anything that I can think of. I don’t really do a whole lot of mobile app testing though, so, that is to say, I don’t do any at all. I used to do a little bit like Bug Bounty, but that was mostly just setting up an emulator and proxying through burp and doing web stuff against mobile apps?
I’m not. That’s the, that’s one of the few things that I don’t actually do a whole lot of hacking on. So. Sorry.
Jason Blanchard
All right, and then. Ryan Poyer, can you please get Tom a link to join us?
Deb Wigley
Yeah, well, I’m from MySpace is here, so.
Jason Blanchard
Yeah, Tom, Tom is watching. He’s not, is not handling. could you. Go ahead.
Deb Wigley
can you talk about some practical ways to prevent DLL hijacking?
Craig Vincent
no, not really. Just make sure you’re not trying to import. Make sure you’re including DLLs. That you’re trying to import with your product. I guess that’s about it. Because there’s other things, like it’s the search order hijacking stuff that’s not necessarily in your control as a developer because that’s all about who’s managing the endpoint.
Letting them write to the system directory is kind of like, what am I supposed to do about that? Well, just make sure your DLLs are there, I guess is the one point that I would recommend.
Jason Blanchard
what’s your biggest secret? You have, I guess, as in the thing that you do that you don’t see other pen testers do.
Craig Vincent
I don’t. I don’t know.
Jason Blanchard
I do.
Craig Vincent
None of us. What, what is it?
Jason Blanchard
You are one of the best report as you go people at Black.
Deb Wigley
Mhm.
Craig Vincent
Because you have to or else bad things happen. Not just, not just, not just angry calls from John, but like, just bad things in general happen. Like document everything as you’re.
As you’re, as you’re working in hacking.
Jason Blanchard
Can you like, emphasize like what it looks like to report as you go? So if you don’t know what I mean by report as you go, Black Hills, John Strand to every pen tester.
We even have a plaque that pen testers get when they get a job here. It goes on the desk. Oh, oh, Craig’s got his report as you go. it is the, it’s the foundation of what Black Hills does.
So Craig, could you emphasize what report as you go really, really means?
Craig Vincent
It, it means just that, I can talk more about the implications. So basically you start off with your methodology. So I’ve got like a framework skeleton of the things that I’m going to do for whatever type of test it is.
And then as I’m walking through my methodology, I am screenshotting and putting narrative for everything that I do so that the report gets kind of built on its, on its own. And then if I find a finding, I just throw in a little finding.
Hey, I found this finding. Look up here for the finding. So then, so by the time you’re actually done hacking, the report’s pretty much written. And then just go through your findings and it makes it really easy to just fill out the finding section.
Then you write your exact summary and it makes it makes life a lot easier. because I guess some people like writing and reporting. And yeah, we get to write about the cool stuff that we did.
But like, I don’t want to like, get to do cool stuff for like the whole test. And then like be stuck trying to write about it after the fact. so writing as you’re doing it keeps you in the moment and it’s almost like, I feel like sometimes even just writing it, it’s almost like if you’ve ever heard of like rubber duck debugging as a developer, where you’re, you’re stuck on a problem and then like, you like talk to your rubber duck on your desk and you explain the problem and then it clicks and you get an idea and you fix it.
That’s the thing, that’s a developer thing. But like just the act of, the act of like writing out the stuff that you’re doing and documenting is almost like your own rubber duck debugging. Like it might give you ideas or spark thoughts or help you figure something out as you’re going.
That doesn’t always happen, but it can happen. So it’s another useful thing. There we go.
Jason Blanchard
Not, to be self promotional. BB King has a report writing class coming up at the Secure Code Summit in December. So, we’ll get a link for that in case you would like to take a report writing class with bb, who is pretty much the person who oversees a lot of the report writing that happens at Black Hills.
Question, do you leverage AI while pen testing?
Craig Vincent
I, do not.
Jason Blanchard
Why not?
Craig Vincent
I just haven’t, I haven’t found. I might soon. So I’ve heard people doing cool stuff with it for getting proof of concept code for like bug bounty exploits.
So I might incorporate it in my methodology. I just haven’t yet. and a lot of, a lot of my writing, I can just, I can write it faster than I can get a machine to write it for me. Plus, I’m not so sure I trust like, what the machine is going to tell me if you prompted it to like give you like technical information.
So unless it’s like code that I can run and test and see if it works or not, I just haven’t messed with it personally. I know some people do, but I have not.
Tom Smith
Craig, can you think of any? I’m kind of curious. Craig, do you have any sort of, hypothetical applications for for AI during testing, even if you haven’t tried them?
Craig Vincent
you could probably help, you could probably help with some explanation of vulnerabilities for like reporting. I’ve heard of a little bit of that, but I mean, obviously you have to like, you have to proofread and check and verify that what it’s giving you is not, garbage and it’s not hallucinating or whatever.
there, the other things that I’ve heard is like people for rapid development of like, little gadgets or scripts or tools they want to write to exploit something or add a functionality for their automation or their workflow or whatever, they can prompt it to provide that code for them and they can rapidly develop from that.
those are applications I’ve already heard of. Like I said, I haven’t thought of any novel ideas, that I would use it for. But I, I don’t know.
Tom Smith
I mean, the other thing, I mean the other thing you got to think of is when, one of the reasons that people come to, there’s plenty of automated tools out there, right? So I mean, you can, you can check, this side or the other thing with automated tools with relative ease.
You don’t even have to be a security professional in a lot of cases. Right. And the reason you come to a third party, pen testing firm or even have a, a pen tester who works inside your organization is because you want the human touch, you want the creativity that’s available.
And so it’s really just a, it’s really just a question of can I ever duplicate that level of creativity? Right. and possibly no. Right? That’s a possibly a never.
So, there comes a time when you got to think that, if the answer is going to be no and it’s never going to be yes. There’s always going to be at least, at least the vast majority of pen testing is probably going to be done by humans.
At least that’s my opinion.
Craig Vincent
I mean, if they, if AI ever takes my job, I’m just going to get good at hacking AI and doing prompt injections. So we’ll fix that right there.
Jason Blanchard
I would like to talk about how Tom appeared like the Smoking man in the X Files and he’s like shadowy.
Deb Wigley
And he’s just a little shadowy.
Tom Smith
Yeah, I know. usually we’re on, usually we’re on Ms. Teams and I’m nice and bright and shiny on teams, but here I am just, in the, in a cave, apparently on Zoom.
Jason Blanchard
So how often do you actually get the source code versus doing black box testing?
Craig Vincent
I’d say 50. 50. I guess I haven’t done a million of these things. I’ve only done like four or five. So, But yeah, 50. 50, I’d say. And I don’t really spend a whole lot of time in the source code.
Unless I see interesting behavior and I want to like deep dive into it or try to trace through where user inputs going or where other inputs are going.
Jason Blanchard
Like do you start to see in code, Craig? Like do you see the world in code now?
Craig Vincent
No, it’s not like the Matrix.
Jason Blanchard
It’s not.
Craig Vincent
No. That’s a good thing. That would suck.
Jason Blanchard
Okay, what is your favorite topic in mathematics?
Craig Vincent
I thought we had a, we had a math logic course that was really interesting. It was required for all CS students, but I minored in math. That was my favorite. I wasn’t a big fan of anything to do with calculus.
All the calc based stuff kind of hurt my brain. But the, the logic stuff was very, it was very it was very interesting and it was very applicable to like coding and computer science type stuff.
So I like that a lot.
Jason Blanchard
Here’s a question. Are you always looking for new tools for your methodology or have you settled into the tools that work and you have enough?
Craig Vincent
It, it’s fits and spurts. I’m always looking for the new hotness. occasionally I feel like, oh man, there’s gotta be a better way or is there anything else? And I’ll occasionally just go look.
So yeah, it’s, it’s iterative. Like I’ll get comfortable with stuff and then as soon as I get comfortable I’m like, okay, is there, can I add to this? Can I, can I make this better? Can I add, can I find something else to improve this as an.
Jason Blanchard
Endorsement here for Discord? If you scroll down on the left hand side, you’ll see the tool sharing, channel. And so lots of people share tools in there, Tools that they find, tools that they think is interesting. If you go down to the infosec slash learn plus share, that’s where all the different categories, are for you to like.
Hey, does anyone know about a tool for this or a tool for this or here’s a tool I found that does this and so it’s a great like place to go and just harvest new tools or tools that people are finding that they really enjoy.
So if you have a tool that you really enjoy, go ahead and drop it in tool sharing to share it with the rest of the community here.
Deb Wigley
This is a interesting question. What emerging tech is making your job harder?
Craig Vincent
I don’t know man. Nothing. Really nothing. I guess like WAFs and CDNs, that’s not really new. They just when you can’t get a customer to get you on an Allow list and let you through them.
They can be kind of a pain. But nothing, nothing like just jumping out that I can think of that’s been like, oh, man, I can’t stand this. interesting.
Tom Smith
Nothing sort of categorically new. Just, no, nothing. Impressions in existing technologies.
Craig Vincent
Yep.
Jason Blanchard
Yeah, Craig, So this was an intro talk. So where do you go to get your intro advice? Like, because you had to start at some point. So where do you go to get started?
Craig Vincent
Google. So, like, it’s like I said, like, I was sitting here and like, I got this, this test coming up, and I’m like, well, I have, this. All these skills and this broad skill set that I know is all applicable, but I don’t know how to organize it.
So the first thing I did was I Googled desktop application pen test methodology. Literally. I think that’s why I typed and there was some stuff out there. And I was like, okay, this is a good starting point.
but that’s literally it. I just start Googling.
Jason Blanchard
if you can’t see all the channels inside Discord, on the screen, what you’re showing right now is you go up to the top where it says Black Hills Infosec. You click that down arrow and then you say, show all channels, and then that will reveal all the channels for you.
So if you say show all channels, because sometimes, they’re like, hey, discord’s overwhelming if you’re new or something. so if you click all channels, you’ll get to see them all. And speaking of which.
Go ahead, Deb.
Deb Wigley
I was saying the tool sharing channel is not private too.
Jason Blanchard
Yeah, it’s not private.
Deb Wigley
It’s for everybody.
Tom Smith
Yeah, it’s for everybody.
Jason Blanchard
if you haven’t checked in for hacket yet, make sure you check in for hacket. All right?
Deb Wigley
what’s hacket? For those who have no idea what you’re talking about.
Jason Blanchard
so Hackett is our way of saying thank you for coming back and coming back and coming back and coming back and coming back at least ten times. Then, you get the access to the Hackett channel, where you can then talk to all the other people who’ve been here more than 10, webcasts.
we send you a reward for 10, 20, 30, 40, and 50. We’re, still working on the reward for 40 and 50, because some of you got there faster than we expected. Thank you.
Deb Wigley
When you get the pizza, we talked about the pizza.
Tom Smith
We talked about it.
Deb Wigley
That’s all we did, though. And then we ate Pizza. but we didn’t actually make a decision.
Jason Blanchard
All right, I’m gonna do one last question.
Deb Wigley
Okay.
Craig Vincent
Hit me.
Tom Smith
Several people typing.
Deb Wigley
Oh, yeah.
Tom Smith
Tough choice, Jason.
Craig Vincent
Okay.
Deb Wigley
Jason, what’s the song of the day?
Jason Blanchard
are there any.
Deb Wigley
You were singing Kumbaya earlier.
Jason Blanchard
We can talk about that.
Deb Wigley
It was very unnerving. It’s the word.
Jason Blanchard
If you click on your name inside Discord, you’ll see how many hackets you’ve already received. and we started last year in November. So if you’re like, I’ve been here for years. I know, but we started in November of last year, so we’re coming up on one full year.
All right, last, question. Are there any tools you would suggest for applications that use a local database, backend any good ways of intercepting the SQL queries that of?
Craig Vincent
I would typically try to go, sorry, there’s a cat outside my window. My cat’s freaking out. I would try to use the native database software, if possible.
that would my go to, like, whatever. It’s like SQL Server. Like, I would try to use whatever is meant to access, and write to the database in the first place, and then just try to get the customer to give me creds or suss out the creds from memory or the source code or whatever, configs, wherever that might be.
Jason Blanchard
I have one last question. This is going to be the last.
Deb Wigley
Okay.
Jason Blanchard
Have you ever broken any functionality while testing which impacted the system or network resources? I, wonder if there’s, like, a client that knows you personally or if.
Craig Vincent
It’S not on a desktop application. Pen test. I’ve knocked some stuff over on other tests before, though not intentionally, of course, but it can happen, unintentionally.
Resource load on servers occasionally. we had one interesting one where they had some kind of load balancer where things that were supposed to be out of scope were getting hit, even though they were not included in the scope for the scans.
So stuff happens, but nothing’s super crazy.
Deb Wigley
one last reminder. Hackett is right now only for Thursday’s webcast, but starting in December. When did we decide?
Jason Blanchard
January.
Deb Wigley
January next 2025. the news on Monday at 5 will also count.
Craig Vincent
Yes. Yes.
Jason Blanchard
All right, so, Craig, what we normally do is we. First of all, thank you. Thank you for coming here. Thank you doing this. Thank you for, answering all the questions that, presented your way.
we appreciate you sharing your knowledge. Thank you for coming here at least once a year and doing these, make sure. You check out Craig’s last webcast on web app. Web, app pen. Testing methodology. All right, so, Craig, if you were going to sum up everything that you talked about here today and one final thought.
What would that be?
Craig Vincent
yeah, I mean, just figure out as much as you can about the application as possible, like, before you get too in the weeds. Otherwise you’re going to sit staring at a debugger for a week and not have anything.
Jason Blanchard
Yeah.
Craig Vincent
So look at all the different attack avenues. Think outside the box.
Jason Blanchard
all right, so what we’re going to do right now is we’re going to essentially end the webcast and say thank you so much for joining us. If you are on Discord, please stick around. Discord, is like, what.
It’s how the community keeps communicating in between the webcasts. Because the webcast lasts about an hour, but Discord lasts for forever. And so that’s a place where you can ask questions, answer questions, and be a part of the community.
Learn as much as you can, dive into the channels, harvest all the information you could possibly learn. This is a place for you to ask questions in a safe place where you’re not going to be judged or someone’s going to think you’re like, I can’t believe you don’t know that.
All right, this is an intro talk. We expect intro knowledge. Right. and so we’re going to end the webcast now, but we’re going to stick around. So we’re sticking around. If you would like to do business with Black Hills at some point in the future for penetration testing, feel free to stick around.
If you want to know what it’s like to do business with. With Black Hills in the future doing penetration testing, then stick around. we are not going to do that while, like, we have you here.
Like, I’ve been a part of other webcasts where, like, the first 30 minutes is a sales pitch and then they talk for 10. that’s not what we’re doing here. We’re giving you a chance to go.
Go, like, leave. Stay in Discord. Stay. Stay in Discord, but leave the webcast because, we don’t want you to be like.
And then they told me about their sales process. that’s. That’s not what this is. Yeah. All right, so I’m gonna give you eight more second.
Seven, six, five, four.
Deb Wigley
They’re leaving.
Jason Blanchard
Okay, so the webcast is over. Craig’s going to stick around a little bit. I don’t know if we have anyone else here, but we got Tom. and you can feel free to ask questions about what it’s like to, hire us to be pen testers.
You can ask those questions inside discord.
Deb Wigley
We have sock, Active sock. We can do instant response.
Tom Smith
Plenty of things. We have many things, many services.
Jason Blanchard
And the reason every once in a while is because people are like, I thought you were, like, you made backdoors and breaches, and you did webcast and like, you had a training organization. I was like, all those things are true.
Tom Smith
And.
Jason Blanchard
And we provide services for people. So this is for those of you that may not know who we are. So, Tom.
Tom Smith
Yeah. Yeah.
Jason Blanchard
Would you. Would you consider yourself a sales bro that works on commission?
Tom Smith
No. No. Zero percent, Jason.
Jason Blanchard
Zero percent.
Tom Smith
No, not at all. No. no, here’s the thing. I mean, ultimately, fhis one thing that we do is kind of make up our own job titles. So, we don’t have any formal job titles or formal reporting relationships or anything.
So, consequently, yeah, I could call myself sales consultant or something, but why? that’s not appealing to anyone.
so, no, we don’t really do any sales. I mean, half the calls that we do, we don’t end up proposing any work to the client. we end up giving out free advice, just having a conversation about what the client thinks next step.
And I shouldn’t even say the word client, about what the person who comes to us thinks are next steps on their sort of journey to security, if you will. So. And you have to forgive me, guys. I really, I promise I don’t live in a cave.
It’s usually like this here.
Deb Wigley
Very dark.
Jason Blanchard
So, Tom, like, if someone wanted to do business with us, step one is probably email consulting or go to the website and do the contact us form and give us a little bit of what they’re looking for.
And then. And then how many times do you hound them until they buy something?
Tom Smith
No, we. We do zero hounding. So, ultimately, like, if you reach out and you say, hey, I want to talk to bhis about this, that, or the other thing, we’ll invite you to schedule a meeting with us and we’ll do.
We’ll do a call, usually half an hour, and then figure, out exactly what it is that you want to talk about in the first few minutes and then spend your time talking about that.
And, that might be a pen test that might be talking about some sort of blue team services. Be that, security, operations center, active sock. It might be continuous testing, that we have through the antisoc, service.
You guys who come to webcasts all probably know Corey Hammer. and then ultimately, trying to figure out what it is that we can do for you. so Jason asked if we do any hounding answers.
No. we’ll invite you to have a call, and if you get cold feet, you don’t want to do it, we’re not going to bother you about it. and if you do want to see some sort of, proposal for us to do some work for you, we’ll send it to you.
And then after that, if you, if you want to do it, we’ll talk about how we can narrow it down and make it exactly what you want and, provide that service. So that’s. That’s ultimately it.
It’s pretty slow pressure, pretty much zero pressure. But, yeah, it’s kind of how we roll. Yeah.
Jason Blanchard
Like, think of it this way. Like, imagine if we were really friendly here, giving out knowledge and doing all these things, and then like, you show up to the sales process, and then it’s, like, overwhelming. And it’s like I saw Black Hills was.
Deb Wigley
And then Tom guy, though.
Tom Smith
Yeah. What a jerk. yeah.
Jason Blanchard
We want to be who you think we are and who we actually are. Yeah, it’s true. So, Tom, let’s say they do schedule something like what happens next.
Right. Because we have Craig here who actually does pen Pen testing. and so, like Tom, do you then connect them with Craig? Does Craig become a part of the call? Like, when does Craig get involved?
Tom Smith
Yeah, so, I mean, when. I’ll say when I was low knowledge and first started, it was like we’d get a lot of help from Craig and company, on calls to figure out what the heck is.
What the heck it is that we can do for you guys. as our team is sort of developed in knowledge that’s a little less frequent than we have to, but we’ll certainly pull testers in.
If you have something that’s like, kind of an edge case or very custom, then we’ll certainly pull them into. Assist in the original scoping, but otherwise you end up working with our team generally.
And then we’ll pull in Craig or other testers when it comes time to establish sort of what the. We want the formal rules of engagement, for the test to be. So when you have.
When we get down to the Nitty gritty of what a pen test or other engagement might look like. Then we’re pulling in. The testers figure out, hey, do you want to do, do you want to do a, a daily meeting during the test?
Do you want to have a slack channel open during the test? what, what IP ranges? Do you want to make sure that we’re not sc. things like that. So when we get down to the nitty gritty, about setup, things like that, that’s usually when you’re going to see the testers get pulled in.
but yeah, if you, if you call in, if you, if you, if you reached out to us and like, hey, I saw this webcast and the thing that Craig talked about, that’s exactly my use case. I’d like to talk to him directly.
we don’t hide the testers technical resources away, so we can certainly pull the right people in, right in the beginning if we need to. Yeah.
Deb Wigley
Well, how often do you have people, request to meet with you who have never had a pen test?
Tom Smith
All the time.
Deb Wigley
All the time.
Tom Smith
Yeah. I mean, if we have, if we meet with, let’s say, 10. Let’s say we, let’s say this week we met with 10 people we had never talked to before.
M. Probably half of them.
Craig Vincent
Interesting.
Tom Smith
Never had a test before.
Deb Wigley
Okay. yeah, I think that’s. Maybe talk a little bit more about that because some people might be fearful or just not even sure what it is and if they need it and.
Yeah, that’s interesting to know that. Half of them.
Tom Smith
Yeah, I mean, that’s, I mean, that’s not even. That’s just anecdota. But. But, yeah, no, I mean, that’s the thing. So, if you’ve never done, a test before, any sort of penetration test on whatever it is that you’re concerned about the security of, be it an application, a network environment, a cloud environment, you’re welcome to reach out and we can talk through kind of what we, we’ll have a conversation for a few minutes, figure out kind of where you stand in terms of security, what’s keeping you up at night, and then ultimately how we can test whether or not this particular thing or that particular thing that you suspect might be a vector, whether it really is.
and then we can sort of match up, match up some kind of tests or write some kind of test that meets your needs in the beginning and the Thing is, we heard about desktop application pen testing today.
Primarily there’s a, bazillion kinds of pen test out there. Right. And so what we’re going to try to do is find the one that fits the needs of the organization we’re talking to.
if it’s a smaller organization, obviously we’re not going to try to push them into like some, ridiculous fancy red team engagement or if you’ve never done a pen test before, how do you get the most value out of it?
Well, you look for the high level, low hanging fruit kind of stuff. And so those are the things that we’re going to try to establish in the first conversation. It’s like, where do you stand? How can we give you the most bang for your buck?
That’s going to put you in a better position so that in the future, not only are you more secure, but should you want to do something else later. How do we position you? How do we help position you to be ready for that thing?
Jason Blanchard
Tom, do we only work with like Fortune 50 companies or do we work with whoever require, like, request us?
Tom Smith
I mean, we work with, if General Motors wants to reach out, we’ll talk to them. Yeah, but if Bob’s Bait Shop wants to reach out, we’ll talk to him. it all depends on, it all depends on, what, what ultimately you want to do.
as long as what you want to do is something that we do and our range of services is pretty broad, then we’ll work with you. we’re not, we’re not fishing for, big name clients.
you don’t have to be fancy or whatever. despite the fact that we have, webcasts and a larger presence, in social media and on the Internet, doesn’t mean that we’re huge and impersonal or whatever.
everybody that you see on this webcast today is just a regular person. So, I mean, except Ryan, but.
Jason Blanchard
Except for Ryan.
Deb Wigley
Another story.
Jason Blanchard
people want to know if your house is haunted, but we’ll come back to that. he’s right now. Yeah, I know it’s Halloween. you ask those kind of questions.
so, Craig, once you give someone the pen test report, what happens at the end is, at the end, do we, like, never see that person again? Is this like we’re breaking up now?
Like, what is the pen test report process? Like?
Craig Vincent
so I really, the way I do it, I mean, everybody’s A little bit different, but for the most part you deliver the report. And I say like, if you have any questions or concerns, we can discuss it if there’s any modifications.
Because the biggest thing is when you do a pen test report, it’s the perspective of the pen tester. And I don’t have the visibility. I, don’t have the ability to see necessarily everything going on in your organization or your systems.
Right. So, a lot of times, like they’ll have questions, they want clarification on vulnerability or finding. they might have questions about methodology, how to recreate things, even though we try to make it as documented and well enough to recreate anything.
But they might have specific questions about how to do certain things. they might have concerns or want to push back on the rating of a severity of a finding.
Right. And that’s not as common, but those are things we can talk about if they’re like, hey, yeah, we have XYZ control and then I can look at it and we can maybe have a conversation about modifying severity.
But that for the most part, yeah, it’s not like you get the report and then see, like you’re never gonna hear from me again. we go over the reports together with customers if they’d like. I always offer that.
But like, hey, we can go over together and walk you through everything that we did. yeah, it’s very much like an ongoing thing.
Jason Blanchard
Mhm. this question just came in, Tom, and I know that this one’s probably pretty close to something we really launched in 2024.
Really? Well, because of the recognition that we’ve gotten in the industry. And it says as an msp, do you guys have any partner or reseller opportunities or how does a, relationship like that typically work?
Tom Smith
Yeah, no, that’s a great question. So, yes, well, we’d be happy to work with you if you’re an msp. So, we do have, admittedly some, we do have some, agreements.
I hesitate to use the word partnerships. We do have agreements with a couple of different MSPs that we work with. we’ve we’ve also, in full disclosure, we’ve found some MSPs that we’ve tried to make things work with and just kind of hasn’t come together.
So, a couple things, we really like to be, we like everything to be sort of aboveboard. So we don’t do white labeling. Right. So we don’t work with an MSP who turns around and Resells our services and then acts like it’s them who did it.
We don’t do that. that’s, that’s sort of one thing we, we don’t really do. We like everything to be aboveboard. Everybody knows who’s who. Everybody, everything’s kind of understood. If you want to resell our services and add value as a var, then we want to make sure that you’re actually adding value and not gouging anyone.
We don’t like to be part of gouging. but beyond that, the more laid back you are and the more willing you are to have open conversations and stuff.
I mean obviously these are your clients. If you’re an msp, we’re not telling you how to manage your clients. But people who are a good cultural fit from us as MSPs tend to be organizations who have sort of the same philosophy and approach as we do, where like to have good open conversations with their clients, understand kind of what their goals are and not be super motivated by the commission.
Obviously we don’t run your company, but cultural fit is a big thing for us in those, in those or in those times when we work with msps.
Jason Blanchard
and then lastly, so if someone works with us and we do a pen test and do you recommend that we keep doing that year after year after year after year after year after year after year?
Tom Smith
The very same pen test? No. Right. So, a couple things. So we have some, we have some organizations that we have worked with for many years and we’ll do a certain particular type of pen test every year, but we’ll do additional services above that, that rotate year to year.
So a good example might be an organization that’s a little larger. Maybe, they want to do an external network penetration test every year. Right. Look at what their footprint looks like on the Internet every year.
Make sure that nothing is snuck in that they’re not really aware of. but they’ll pick a project every year and we’ll work with them. Say like, okay, this year we’re going to work on this application, we’re going to take a look, make sure this application is as secure as you think it is.
And then next year we’ll do like a wireless network penetration test. And the year after that we’ll do maybe, some, maybe we’ll look at their AWS environment, something like that. So there are some tests which are kind of evergreen, right?
a good one might be an assumed compromise we could look for different paths and we looked for in previous years, but at the same time, no, we don’t want to just do the same dang test every year. That doesn’t make sense. I mean, if you haven’t had, any real change year over year between an environment, it doesn’t really make a lot of sense to pour a bunch of time and money and effort into that when there’s other things that you might test that are likely to be more fruitful ground for finding room for growth and security.
Craig Vincent
Unless compliance says you have to.
Tom Smith
Craig, hit the nail on the head. That’s right. Well, we’re here for our annual external and internal pen test, guys. So just, give us the same thing that we got last year. We do hear that.
And you can’t get around that.
Jason Blanchard
All right, Deb, did you see any other questions or have any questions of your own?
Deb Wigley
I think no, just a lot of really well placed memes. is what. I’m so well done with the meme. I think we’re good.
Jason Blanchard
Okay. and then, this isn’t like one of those, I said it last time, right? It’s like, not a Jerry Lewis marathon telethon or something. It’s, But for the people who’ve already reached out to us who are like, hey, I’m interested in pen test.
Thank you so much for reaching out. For those of you that have been customers of ours, clients of ours, thank you for your trust in us and for those of you considering, us in the future, we appreciate you trusting us enough to even, like, start thinking about the process.
Right. Because being a pen test firm is all built on trust. You are allowing us to come into your home and look and see what we can find. And we know that that takes a lot of trust on your part, and so we appreciate the trust that you’ve given us, will give us potentially considering giving us.
So thank you so much for that, and hopefully, we’ll continue earning your trust over time. All right, with that, I think we’re. Happy Halloween.
Deb Wigley
Happy Halloween.
Jason Blanchard
Yeah. All right. Kill it, Ryan. Kill with fire.