Go-Spoof: A Tool for Cyber Deception
Ben Bowman is a Security Analyst at Black Hills Information Security. He graduated in 2024 with a degree in cyber operations. Ben conducts research as well as tool development outside of testing.

As an attacker, you value speed and silence when conducting an attack. But what happens if you’re scanning a host for service banners and every port is open? The scan takes an endless amount of time; why would every port be open?! It’s frustrating and disorienting. It forces the attack to be louder and more aggressive, and BOOM! The SOC notices your presence and isolates you, ending your attack.
Go-Spoof
The scenario above demonstrates the perspective of an adversary against cyber deception. As a security researcher, I have studied the efficacy of cyber deception and found it to be extremely beneficial, increasing detection and reducing compromise.1 In hope of reinvigorating interest in an otherwise lacking area of cyber, Joe Boyd and I have revitalized the classic tool Portspoof into Go-Spoof.
Key Features of Go-Spoof
Go-Spoof brings an old tool to a new language. The Golang rewrite provides similar efficiency and all the same features of the previous tool but with easier setup and useability. With this tool, all 65,535 ports on your machine appear open and complete with fake banners and service versions, hiding anything real on your network and wasting attackers’ precious time and tiring them out.
Who Can Benefit from Go-Spoof?
This tool hardens your Linux machines with security through deception. It benefits a wide variety of demographics, from system administrators to researchers. This tool can provide a leg up at king-of-the-hill-style CTF competitions, wasting opponents limited competition time by prolonging scan time and inundating them with fake services. If you know someone wants to get into your network, ruin their day with Go-Spoof.
Getting Our Hands Dirty
Installing this tool is straightforward. First, we need to pull the repo from GitHub.
git clone https://github.com/blackhillsinfosec/go-spoof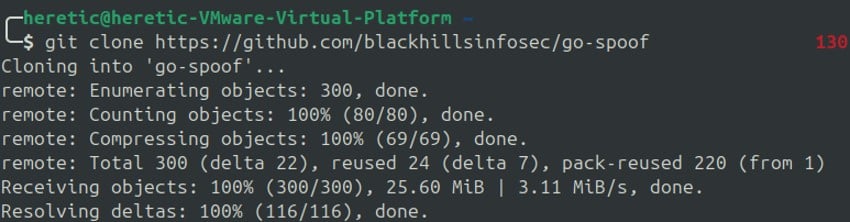
cd /go-spoof/srcThen you can run the tool by using the following commands.
sudo iptables -t nat -A PREROUTING -p tcp -m tcp --dport 1:65535 -j REDIRECT --to-ports 4444./goSpoof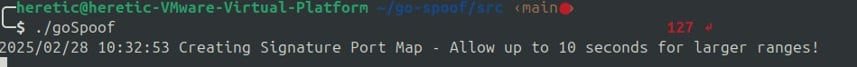
“But Ben, I don’t want to set the tool up to test it…” I understand that! Try Nmap scanning bhis.tech with the following command to see what it looks like from an attacker perspective.
nmap -p1-100 bhis.tech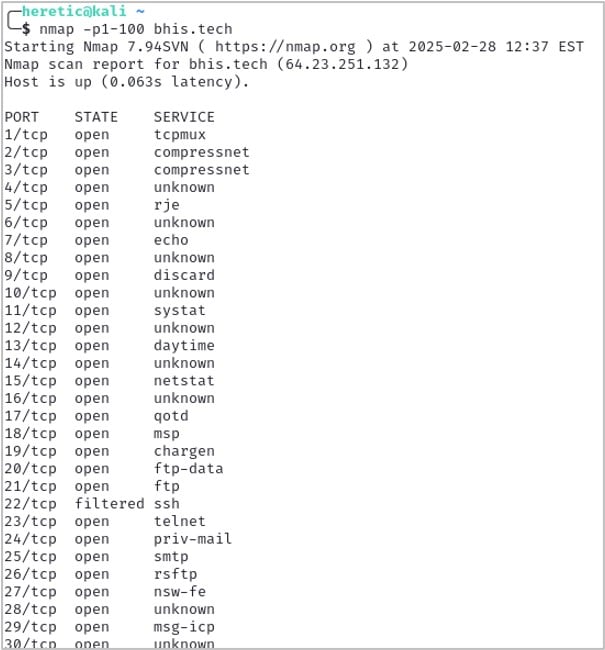
Conclusion
By increasing the ease of use of a classic tool, we hope that Go-Spoof not only helps peak interest in cyber deception as a legitimate defensive measure but also makes it more accessible to the cybersecurity community. Go-Spoof is fully open source, so feel free to experiment and make your own improvements!
Footnote
- https://www.semanticscholar.org/paper/Cyber-Deceptive-Countermeasures%E2%80%99-Effects-on-Attacks-Bowman-Thomas/b169c6840be7b9703275daf7c5592094f75853f3?utm_source=direct_link ↩︎
Want to learn more from Ben?
Register now for his Antisyphon Anticast, taking place Thursday, April 2nd, at 12:00PM EDT: