WEBCAST: Two Covert C2 Channels
John Strand // In this webcast, we walk through different tools to establish and test your Command and Control (C2) detection capabilities. Why does this matter? Almost all organizations we […]

John Strand // In this webcast, we walk through different tools to establish and test your Command and Control (C2) detection capabilities. Why does this matter? Almost all organizations we […]

John Strand // It’s odd, we try to push security forward through standards like NIST, the Critical Controls, and PCI, but most organizations strive to meet the bare minimum required […]

John Strand // Want to get started on a hunt team and discover “bad things” on your network? In this webcast, we will walk through the installation and usage of […]
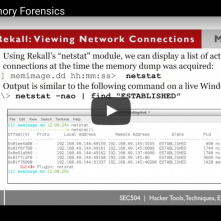
John Strand // In the last webcast we covered initial Windows Live Forensics (see the recording here), in this one we play with memory from a compromised system. We cover the […]

John Strand // So you think you might have a compromised Windows system. If you do, where do you start? How would you review the memory of that system? What […]
John Strand with BHIS testers // Yes, we did this in 2017, but it’s reflecting work done in 2016.
Check out Carrie’s demo of her DPAT, and if you missed her blog, check that out here.
The webcast John did with Paul and Security Weekly a few weeks ago. Better late than never though, are we right??
A bit delayed but here is the webcast John did with Security Weekly and Endgame about Threat Hunting on 11/15/16.