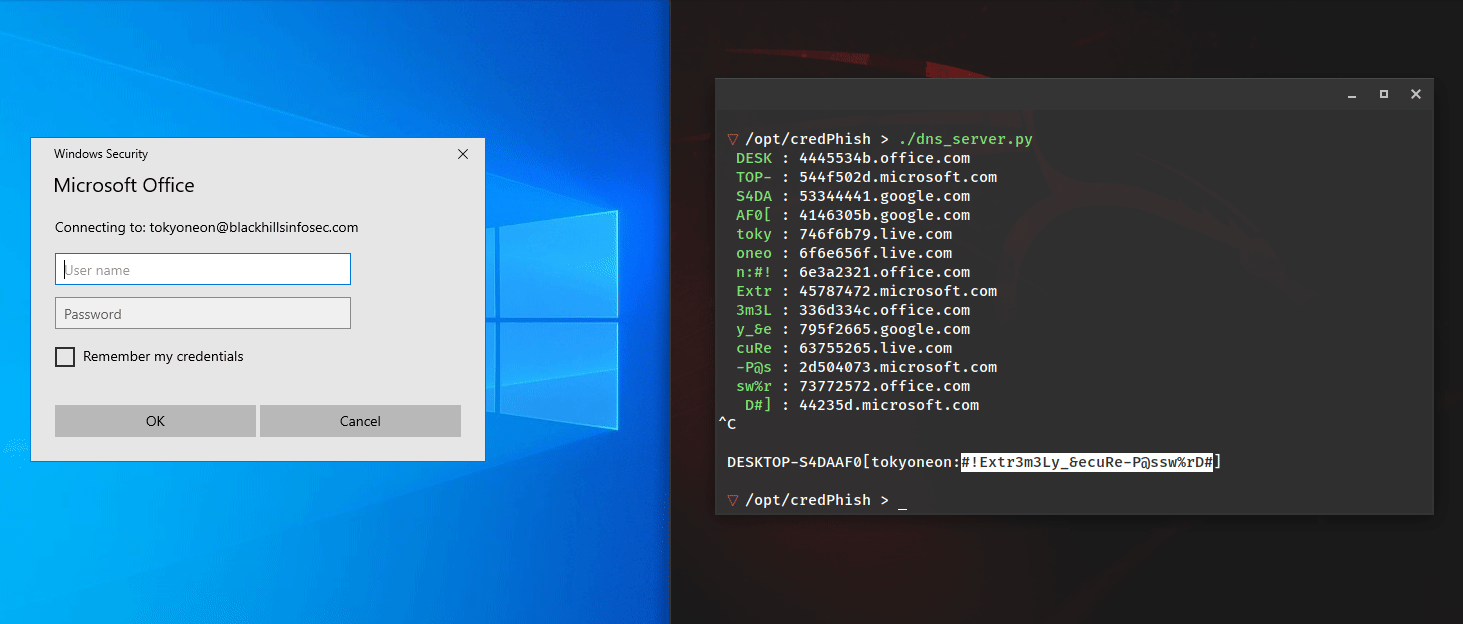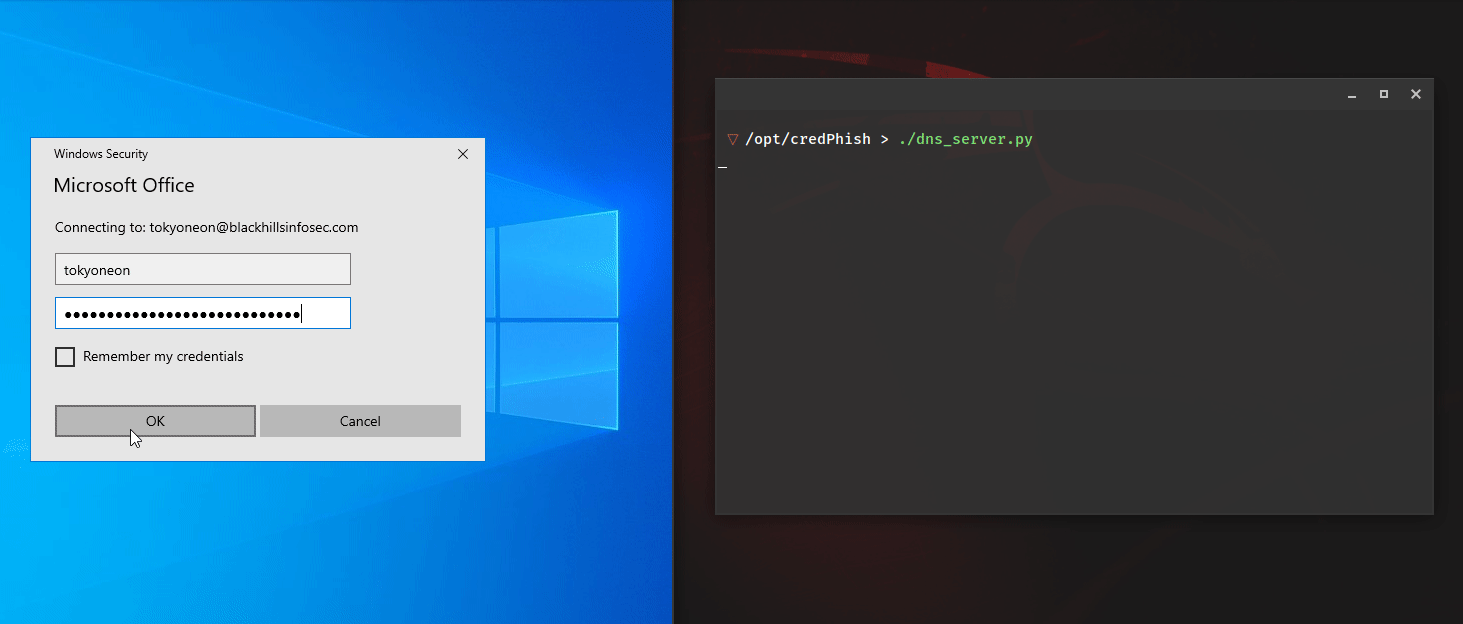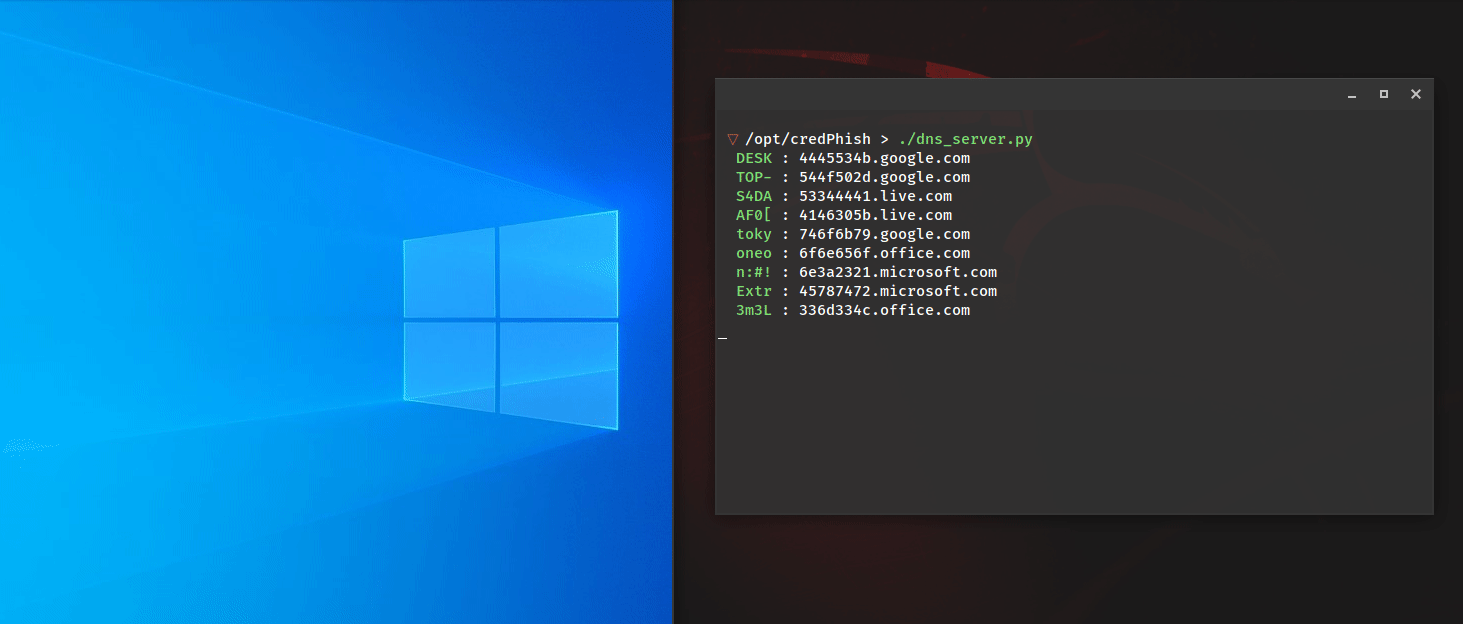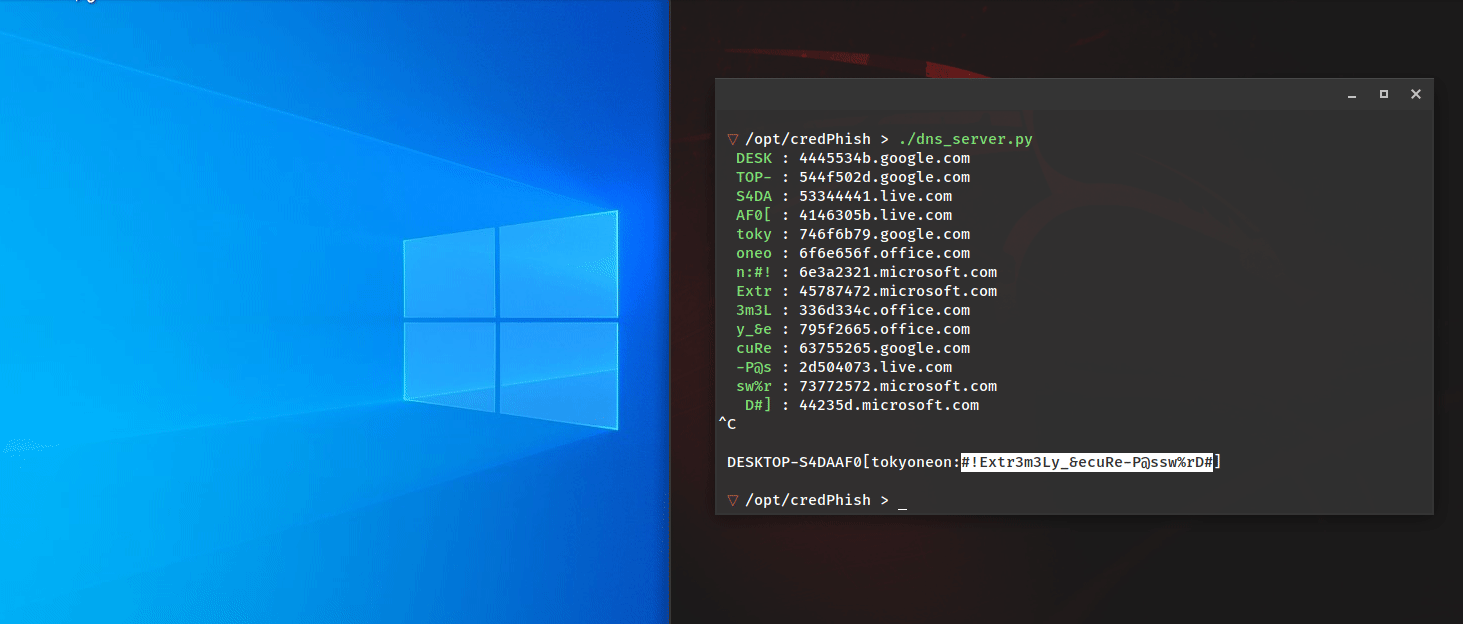
Introducing LoRa (Long Range) Wireless Technology – Part 1
Ray Felch // This write-up is the first of a multi-part series, providing an introduction to LoRa wireless technology and the LoRaWAN, low-power wide-area network (LPWAN). Interestingly, I came across […]