WEBCAST: Proper Active Defense and the New ACDC Active Defense Law
John Strand// In this webcast John talks about the new ACDC law and what it means exactly. There has been quite a bit of anger and great GIFs about hacking […]

John Strand// In this webcast John talks about the new ACDC law and what it means exactly. There has been quite a bit of anger and great GIFs about hacking […]
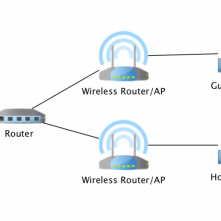
Ethan Robish // In this series of posts, I’ll discuss how I segmented my home network using VLANs and how I moved away from using a risky consumer-grade router at […]

Jordan Drysdale // The following content is loosely based on a presentation I gave at BSides Denver. After speaking at BSides Denver, one of the audience members spent some time […]

David Fletcher// My wife and I recently purchased a 2016 Ford Flex to replace an aging version of the same make and model that met an untimely fate. During the […]

CJ Cox // We frequently get requests from customers asking us if we provide consultation defending their systems. The other day I got a question from a customer asking us […]

Brian King // On a recent webapp test, I got a little frustrated with all the extra HTTP requests showing up in my Burpsuite Proxy History from connections that Firefox […]

John Strand// We just finished up a walk through of how we bypassed Cylance in a previous engagement. To conclude this exciting week, I want to share a few comments […]

John Strand // It’s odd, we try to push security forward through standards like NIST, the Critical Controls, and PCI, but most organizations strive to meet the bare minimum required […]
Sally Vandeven & the BHIS Team // I was recently on an assessment where I was able to grab all the password hashes from the domain controller. When I extracted the hashes and […]