Small and Medium Business Security Strategies: Part 1
Jordan Drysdale// Blurb: A few of us have discussed the stress that small and medium business proprietors and operators feel these days. We want to help stress you out even […]

Jordan Drysdale// Blurb: A few of us have discussed the stress that small and medium business proprietors and operators feel these days. We want to help stress you out even […]
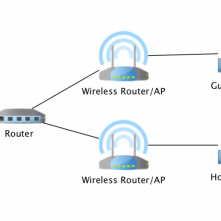
Ethan Robish // In this series of posts, I’ll discuss how I segmented my home network using VLANs and how I moved away from using a risky consumer-grade router at […]

Joff Thyer // I had an interesting experience recently that reminded me to always “trust but verify.” Let me set the stage for you. As a penetration tester, and IT […]

Carrie Roberts* // (Updated, 2/11/2019) Trying to figure out the password for a password protected MS Office document? This free solution might do the trick. It attempts to guess the password […]

David Fletcher// This blog post is going to illustrate setting up a software access point (AP) on Ubuntu 16.04. Having the ability to create a software AP can be very […]

Lee Kagan* // Deploying an offensive infrastructure for red teams and penetration tests can be repetitive and complicated. One of my roles on our team is to build-out and maintain […]

Kent Ickler // Referrer-Policy, What-What? Referrer-Policy is a security header that can (and should) be included on communication from your website’s server to a client. The Referrer-Policy tells the web browser […]

Kent Ickler // Content-Security-Policy-What-What? Content-Security-Policy is a security header that can (and should) be included on communication from your website’s server to a client. When a user goes to your […]

Kent Ickler // In my recent post, we installed and got Cacti up and running. Now, we’re going to add our first switch into Cacti’s services. Switch: This is an HP-Procurve line […]