How To Do Endpoint Monitoring on a Shoestring Budget – Webcast Write-Up
Joff Thyer & Derek Banks // Editor’s Note: This is a more in-depth write-up based on the webcast which can be watched here. As penetration testers, we often find ourselves […]

Joff Thyer & Derek Banks // Editor’s Note: This is a more in-depth write-up based on the webcast which can be watched here. As penetration testers, we often find ourselves […]
Derek Banks & Joff Thyer // If you’re not currently logging and monitoring the Windows endpoints on the edge of your network you are missing valuable information that is not […]

John Strand // In this webcast, we walk through different tools to establish and test your Command and Control (C2) detection capabilities. Why does this matter? Almost all organizations we […]
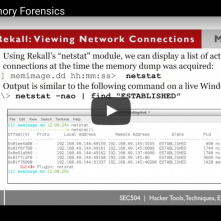
John Strand // In the last webcast we covered initial Windows Live Forensics (see the recording here), in this one we play with memory from a compromised system. We cover the […]
Check out Carrie’s demo of her DPAT, and if you missed her blog, check that out here.

Joff Thyer // It is no secret that PowerShell is increasingly being used as an offensive tool for attack purposes by both Red Teamers and Criminals alike. Thanks to […]
Carrie Roberts // A tool to generate password usage statics in a Windows domain based on hashes dumped from a domain controller. The Domain Password Audit Tool (DPAT) is a […]
John Strand // Lets take a look at how to use HoneyPorts on the new Active Defense Harbinger Distribution. For those of you who do not know, this is a […]

Jordan Drysdale // Life as a ‘blue-teamer’ can often be a stressful experience. Working in an environment with a strong Linux infrastructure can help some, but Ansible can help […]