BHIS Webcast: Tracking Attackers. Why Attribution Matters and How To Do It.
In this BHIS webcast, we cover some new techniques and tactics on how to track attackers via various honey tokens. We cover how to track with Word Web Bugs in ADHD and […]

In this BHIS webcast, we cover some new techniques and tactics on how to track attackers via various honey tokens. We cover how to track with Word Web Bugs in ADHD and […]

John Strand// In this webcast, John walks through a couple of cool things we’ve found useful in some recent network hunt teams. He also shares some of our techniques and […]
Beau Bullock, Brian Fehrman, & Derek Banks // Pentesting organizations as your day-to-day job quickly reveals commonalities among environments. Although each test is a bit unique, there’s a typical path […]
Derek Banks // I want to expand on our previous blog post on consolidated endpoint event logging and use Windows Event Forwarding and live off the Microsoft land for shipping […]

Derek Banks, Beau Bullock, & Brian Fehrman // Our clients often ask how they could have detected and prevented the post-exploitation activities we used in their environment to gain elevated […]

This is the in-studio version of our live in DC event from July. In this webcast, John covers how to set up Active Directory Active Defense (ADAD) using tools in […]
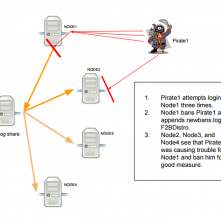
Kent Ickler // How to Configure Distributed Fail2Ban: Actionable Threat Feed Intelligence Fail2Ban is a system that monitors logs and triggers actions based on those logs. While actions can be […]
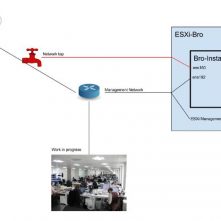
Kent Ickler // You’ve heard us before talk about Bro, an IDS for network monitoring and analysis. We’ve had several installs of Bro over time here at BHIS. It’s about […]

John Strand // In this webcast John covers how to set up Active Directory Active Defense (ADAD) using tools in Active Defense Harbinger Distribution (ADHD) and talks about potential active […]