My Ransomware Post-Mortem
Cody Smith* // As information security professionals we’re not invincible to breaches. Even the most robust security system can’t make up for a lack of user education, which I was […]
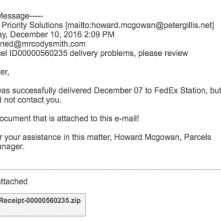
Cody Smith* // As information security professionals we’re not invincible to breaches. Even the most robust security system can’t make up for a lack of user education, which I was […]
Check out Carrie’s demo of her DPAT, and if you missed her blog, check that out here.

Joff Thyer // It is no secret that PowerShell is increasingly being used as an offensive tool for attack purposes by both Red Teamers and Criminals alike. Thanks to […]
A bit delayed but here is the webcast John did with Security Weekly and Endgame about Threat Hunting on 11/15/16.
Carrie Roberts // A tool to generate password usage statics in a Windows domain based on hashes dumped from a domain controller. The Domain Password Audit Tool (DPAT) is a […]
Kent Ickler // As a start to a series on Windows Administration in the eyes of a security-conscious “Windows Guy” I invite you on configuring AD DS PSOs (Password Security […]

Logan Lembke // Step One: Power. Step Two: Enter. Step Three: ???? Step Four: Profit. In the security industry, we love our encryption. However sometimes, the complexity introduced by encryption […]

David Fletcher & Sally Vandeven // We gave a presentation at the GrrCon hacker conference in Grand Rapids, MI on October 6, 2016. The presentation was a dialogue meant to illustrate the […]
John Strand // Lets take a look at how to use HoneyPorts on the new Active Defense Harbinger Distribution. For those of you who do not know, this is a […]