Home Network Design – Part 1
Ethan Robish // In this series of posts, I’ll discuss how I segmented my home network using VLANs and how I moved away from using a risky consumer-grade router at […]
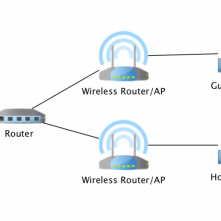
Ethan Robish // In this series of posts, I’ll discuss how I segmented my home network using VLANs and how I moved away from using a risky consumer-grade router at […]
John Strand // I wanted to take a few moments and address the “Hacking Back” law that is working people up. There is a tremendously well-founded fear that this law […]

Beau Bullock & Michael Felch // Source: https://chrome.google.com/webstore/detail/google-calendar-by-google/gmbgaklkmjakoegficnlkhebmhkjfich Overview Google Calendar is one of the many features provided to those who sign up for a Google account along with other popular […]

John Strand// As part of the BHIS Webcast World Tour, we held a live event at the newly opened Arizona Cyber Warfare Range (AZCWR) in Phoenix AZ. To read about and […]

This week we went down to Phoenix Arizona where we teamed up with the Arizona Cyber Warfare Range (AZCWR) for a great event at Grand Canyon University! Black Hills Information […]

Joff Thyer // I had an interesting experience recently that reminded me to always “trust but verify.” Let me set the stage for you. As a penetration tester, and IT […]

CJ Cox// Are you about to have your first pen test? It can be a little overwhelming as a lot of people are sure they’re going to be destroyed in […]
Beau Bullock, Brian Fehrman, & Derek Banks // Pentesting organizations as your day-to-day job quickly reveals commonalities among environments. Although each test is a bit unique, there’s a typical path […]
Derek Banks // I want to expand on our previous blog post on consolidated endpoint event logging and use Windows Event Forwarding and live off the Microsoft land for shipping […]