WEBCAST: Your 5 Year Plan into InfoSec
John Strand // New to InfoSec? Mentoring someone new to the industry? Here’s John’s advice if he had to do it all over again. Sierra is on replying to your […]

John Strand // New to InfoSec? Mentoring someone new to the industry? Here’s John’s advice if he had to do it all over again. Sierra is on replying to your […]

John Strand // In this webcast John covers how to set up Active Directory Active Defense (ADAD) using tools in Active Defense Harbinger Distribution (ADHD) and talks about potential active […]

John Strand // In this webcast, we walk through different tools to establish and test your Command and Control (C2) detection capabilities. Why does this matter? Almost all organizations we […]

John Strand// We just finished up a walk through of how we bypassed Cylance in a previous engagement. To conclude this exciting week, I want to share a few comments […]

John Strand // It’s odd, we try to push security forward through standards like NIST, the Critical Controls, and PCI, but most organizations strive to meet the bare minimum required […]

John Strand // Want to get started on a hunt team and discover “bad things” on your network? In this webcast, we will walk through the installation and usage of […]
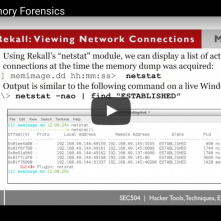
John Strand // In the last webcast we covered initial Windows Live Forensics (see the recording here), in this one we play with memory from a compromised system. We cover the […]

John Strand // There have been a few conversations at conferences and meet-ups over the past year or so about the validity of penetration testing. There are many things on […]

John Strand // So you think you might have a compromised Windows system. If you do, where do you start? How would you review the memory of that system? What […]