How to DIY a Mobile Hacking Platform – Kali NetHunter on a Rooted Nexus7
Derek Banks // As pentesters, it is probably not a surprise that we tend to make fairly heavy use of Kali Linux on a fairly regular basis. The folks at Offensive […]

Derek Banks // As pentesters, it is probably not a surprise that we tend to make fairly heavy use of Kali Linux on a fairly regular basis. The folks at Offensive […]

Joe Gray* // You may have heard about a new genealogy tool called Family Tree Now. It is a (seemingly) 100% free tool (more on that later) that allows you to […]

Brian Fehrman // As described in my last blog post, Powershell Without Powershell – How To Bypass Application Whitelisting, Environment Restrictions & AV (sheeesh…it’s been a bit!), we are seeing more environments in […]

Joff Thyer // Editor’s Note: This is part 3 of a 3 part series. Part 1 discussed configuring your virtual machine engine and virtual hardware emulation. Part 2 covered installing Android […]

John Strand // So you think you might have a compromised Windows system. If you do, where do you start? How would you review the memory of that system? What […]

Joff Thyer // Editor’s Note: This is part 2 of a 3 part series. Part 1 discussed configuring your virtual machine engine and virtual hardware emulation. Part 2 (this part) covers […]

Joff Thyer // Editor’s Note: This is part 1 of a 3 part series. Part 1 will discuss configuring your virtual machine engine and virtual hardware emulation. Part 2 covers installing […]

Luke Baggett // Imagine a scenario where a Penetration Tester is trying to set up command and control on an internal network blocking all outbound traffic, except traffic towards a […]
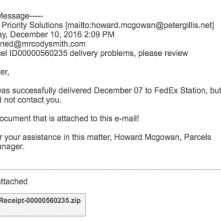
Cody Smith* // As information security professionals we’re not invincible to breaches. Even the most robust security system can’t make up for a lack of user education, which I was […]