Social Engineering – Sometimes It’s Too Easy
Carrie Roberts // A fun story from an adventure in social engineering not too long ago. Thought I’d pass on some things I learned and ways to be more prepared in the […]

Carrie Roberts // A fun story from an adventure in social engineering not too long ago. Thought I’d pass on some things I learned and ways to be more prepared in the […]

Carrie Roberts // Unauthenticated Remote Code Execution? A hacker’s best friend. And that is what we have with CVE-2017-5638 Apache Struts with working exploit code here: https://github.com/rapid7/metasploit-framework/issues/8064 Save the exploit […]

Jordan Drysdale // The Wi-Fi travel kit part one was popular enough that, back by demand, here are the specific parts, part numbers and links. Pretty much everything on the list […]

Carrie Roberts // OS Command Injection is fun. I recently found this vulnerability on a web application I was testing (thanks to Burp Suite scanner). I was excited because I […]

John Strand // Want to get started on a hunt team and discover “bad things” on your network? In this webcast, we will walk through the installation and usage of […]

Sierra Ward // We’re getting to that stage of life where we have to make some hard decisions regarding our parents. How do we help them through sickness? When and […]

Sally Vandeven // Back in November Beau Bullock wrote a blog post describing how his awesome PowerShell tool MailSniper can sometimes bypass OWA portals to get mail via EWS if […]
Sally Vandeven & the BHIS Team // I was recently on an assessment where I was able to grab all the password hashes from the domain controller. When I extracted the hashes and […]
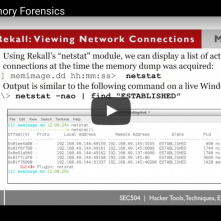
John Strand // In the last webcast we covered initial Windows Live Forensics (see the recording here), in this one we play with memory from a compromised system. We cover the […]