WEBCAST: Your 5 Year Plan into InfoSec
John Strand // New to InfoSec? Mentoring someone new to the industry? Here’s John’s advice if he had to do it all over again. Sierra is on replying to your […]

John Strand // New to InfoSec? Mentoring someone new to the industry? Here’s John’s advice if he had to do it all over again. Sierra is on replying to your […]
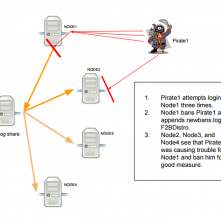
Kent Ickler // How to Configure Distributed Fail2Ban: Actionable Threat Feed Intelligence Fail2Ban is a system that monitors logs and triggers actions based on those logs. While actions can be […]
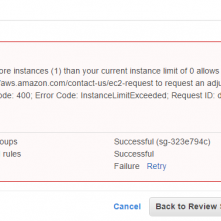
Carrie Roberts* // How does password cracking in the cloud compare to down here on earth? Maybe not as heavenly as imagined. I saw this on the web and got […]

Dear BHIS, So I’m a big fan of you guys! I took John’s SANS504 OnDemand class and I saw the light. Now what? I want to get into security, (maybe […]

Lee Kagan* // Deploying an offensive infrastructure for red teams and penetration tests can be repetitive and complicated. One of my roles on our team is to build-out and maintain […]

Kent Ickler // Referrer-Policy, What-What? Referrer-Policy is a security header that can (and should) be included on communication from your website’s server to a client. The Referrer-Policy tells the web browser […]

Kent Ickler // Content-Security-Policy-What-What? Content-Security-Policy is a security header that can (and should) be included on communication from your website’s server to a client. When a user goes to your […]

Jordan Drysdale & Kent Ickler // In this webcast, we demonstrate some standard methodologies utilized during an internal network review. We also discuss various tools used to test network defenses […]

Joff Thyer & Derek Banks // Editor’s Note: This is a more in-depth write-up based on the webcast which can be watched here. As penetration testers, we often find ourselves […]