A Morning with Cobalt Strike & Symantec
Joff Thyer // If you have been penetration testing a while, you likely have ended up in a Red Team situation or will be engaged in it soon enough. From […]

Joff Thyer // If you have been penetration testing a while, you likely have ended up in a Red Team situation or will be engaged in it soon enough. From […]
Sierra Ward with help from all // Wow, another year, another Christmas and another chance to be totally stumped by what to get you favorite InfoSecker. But fear not! We are […]
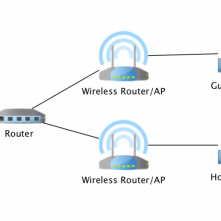
Ethan Robish // In this series of posts, I’ll discuss how I segmented my home network using VLANs and how I moved away from using a risky consumer-grade router at […]
John Strand // I wanted to take a few moments and address the “Hacking Back” law that is working people up. There is a tremendously well-founded fear that this law […]

Carrie Roberts* // I have added resource file and autorun functionality to PowerShell Empire. Empire now has the ability to run multiple commands at once by specifying the commands in […]
Derek Banks // I want to expand on our previous blog post on consolidated endpoint event logging and use Windows Event Forwarding and live off the Microsoft land for shipping […]

Derek Banks, Beau Bullock, & Brian Fehrman // Our clients often ask how they could have detected and prevented the post-exploitation activities we used in their environment to gain elevated […]

Mike Felch // Meet ‘The Box’ Bomb For the last few years at the security conference DEF CON in Las Vegas, the Tamper Resistant Village has hosted a challenging contest called […]