WEBCAST: How Threat Intelligence Can Go Wrong
The webcast John did with Paul and Security Weekly a few weeks ago. Better late than never though, are we right??
The webcast John did with Paul and Security Weekly a few weeks ago. Better late than never though, are we right??
A bit delayed but here is the webcast John did with Security Weekly and Endgame about Threat Hunting on 11/15/16.
Carrie Roberts // A tool to generate password usage statics in a Windows domain based on hashes dumped from a domain controller. The Domain Password Audit Tool (DPAT) is a […]
Here’s our webcast with Beau Bullock, Brian Fehrman & Carrie Roberts from Tuesday, November 29.
Carrie Roberts // Getting a shell using a malicious Outlook rule is an awesome tool during a pentest and great fun! Nick Landers had a great post including enough information to make […]
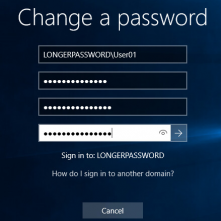
Kent Ickler // As a start to a series on Windows Administration in the eyes of a security-conscious “Windows Guy” I invite you on configuring AD DS PSOs (Password Security […]
Carrie Roberts* // Using a trusted certificate and non-default Empire options will help increase your chances of getting a successful session out of a network. Follow these instructions to get […]
Ethan Robish // In my last two posts I showed how to insert tracking bugs in both .docx (Part 1) and .xlsx files (Part 2). But don’t let all that effort go […]
Carrie Roberts // Tired of typing those Empire commands to startup your goto listeners? Wish there was an equivalent to Metasploit resource files for Empire? This is not currently […]