WEBCAST: RITA
John Strand // Want to get started on a hunt team and discover “bad things” on your network? In this webcast, we will walk through the installation and usage of […]

John Strand // Want to get started on a hunt team and discover “bad things” on your network? In this webcast, we will walk through the installation and usage of […]

Sierra Ward // We’re getting to that stage of life where we have to make some hard decisions regarding our parents. How do we help them through sickness? When and […]

Sally Vandeven // Back in November Beau Bullock wrote a blog post describing how his awesome PowerShell tool MailSniper can sometimes bypass OWA portals to get mail via EWS if […]
Sally Vandeven & the BHIS Team // I was recently on an assessment where I was able to grab all the password hashes from the domain controller. When I extracted the hashes and […]
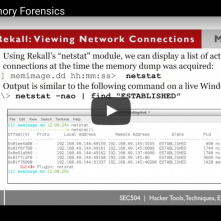
John Strand // In the last webcast we covered initial Windows Live Forensics (see the recording here), in this one we play with memory from a compromised system. We cover the […]

Jordan Drysdale // Sally and I recently ventured to an on-site wireless engagement with a very security-mature customer. Long story short, the level of protection that WPA2 Enterprise with certificate validation provides […]

John Strand // There have been a few conversations at conferences and meet-ups over the past year or so about the validity of penetration testing. There are many things on […]

Brian King // I use GNU Screen mainly to prevent processes from dying when I disconnect from an SSH session, but GNU Screen can do a whole lot more than that […]

Derek Banks // As pentesters, it is probably not a surprise that we tend to make fairly heavy use of Kali Linux on a fairly regular basis. The folks at Offensive […]