Small and Medium Business Security Strategies: Part 3

Blurb: A few of us have discussed the stress that small and medium business proprietors and operators feel these days. We want to help stress you out even more. Not really, but if you aren’t worrying about IT security, you are probably doing it wrong. This series will run through some of the important controls that IT pros have mapped out for us. We are trying to present these in a way that you can accomplish them without dedicated IT staff.
Part 1 – Introduction to SMB InfoSec Controls
Part 2 – Inventory controls of your network hardware #CIS Critical Control 1#
Inventory Part 2, Software
You can do it!
You started this process by introducing your employees to a new year with an expectation that they are now participants in an information security transformation at your company. You should have gathered hardware inventory and contact information for the hardware your company owns and leases. You may have reached out to your various managed services vendors to find out what they know about your network.
Next up: the software that keeps your business operational. As a small business owner, software maintenance can be a disaster. You thought an IRS audit was bad? Anyone ever received a Microsoft audit request form? Plain and simple, if you are running individually installed, licensed and managed Microsoft Office products, STOP. It’s time to budget for new systems that are licensed for Windows 10 Pro and go get Office 365. This will put your life in an entirely new focus. This operating system will keep itself patched, updated and rebooted with minimal effort. The Office 365 product suite, once up and running will do the same, sans the reboots.
If you are reading these in order, the Hardware Inventory post included spreadsheet examples. Here’s another one with prime examples of a software inventory list that most small and medium networks can start with:
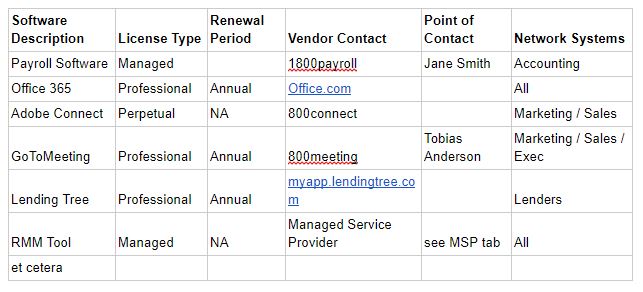
This is going somewhere, and it will matter later. If the implementation of the first five from CSC 20 has you questioning your sanity, take a step back and another deep breath. This is the easy part. Each department has unique needs. Each department probably needs unique software. No one should have the privilege to install software at will. With a simple list of what software goes with which department, you no longer have to allow Bob, head janitor, full privilege to install who knows what on his system.
The goal is to limit exposure and maintain accurate software inventory to allow an organization to secure system configurations. If you don’t know which departments need which software, then everyone gets to be an admin and a single successful phish is likely game over. This inventory management step is critical to ensure that no one on the network needs local administrator. If you don’t know why this matters, if someone with local admin privilege clicks a link, the first adversary tactic is to get local administrator privilege. With this access, all authenticated sessions are visible and those passwords are compromised. This can lead to domain takeover and worse.
Is Managed IT Services sounding better?
Want to learn more mad skills from the person who wrote this blog?
Check out these classes from Jordan and Kent:
Assumed Compromise – A Methodology with Detections and Microsoft Sentinel
Available live/virtual and on-demand!

